CEH Training in Mumbai - C|EHv12
(Certified Ethical Hacker) Course
Course Fees: INR 15,000/-
CEH Training in Mumbai by Indian Cyber Security Solutions is your gateway to ethical hacking expertise, guided by a team of over 130 skilled trainers dedicated to your success. Proudly recognized among the "10 Most Promising Cybersecurity Consultants for 2023" by Silicon India, showcasing our commitment to excellence in cybersecurity training. Our CEH exam preparation training opens doors to networking opportunities, connecting you with like-minded professionals worldwide.
Our three-month CEH Exam Preparation Training, available both online and in classrooms, ensures a practical and insightful learning experience for both beginners and experienced individuals. Our CEH Exam Preparation Training in Mumbai is a testament to our dedication. But here's the real deal-breaker – we don't just teach; we open doors to fantastic job opportunities for you. Beyond teaching, we actively assist you in finding exciting job opportunities, bridging the gap between learning and real-world application. Our focus on practical skills, experienced instructors, and post-training support distinguishes us as the ideal choice for those seeking comprehensive CEH exam preparation. Receive personalized advice, career insights, and practical tips to enhance your understanding of ethical hacking. Join the ranks of approximately 1890 students worldwide who trust Indian Cyber Security Solutions as the ultimate destination for effective CEH training in Mumbai.
Enroll for
Online Live Class
Get Started with FREE Demo Class
Note: "Certified Ethical Hacker" and "CEH" is a registered trademarks of EC-Council and this course is not licensed, endorsed, or affiliated with EC-Council in any way.
UNIVERSITY TRAINING PARTNER'S
Key Highlights
No Cost EMI & Educational Loan
100% Placement Support
3 Months Training
Classroom Training
Online Training
Program Duration
3 Months
Get First 2 Classes FREE
Enroll Now !!
Please contact us using the form below
No Advance Payment Required
Learning Format
Classroom & Online
Why Join CEH Training at ICSS

Reviews
4.8
1,09,233
Students Enrolled in
Indian Cyber Security Solutions

Reviews
4.8
CEH Course in Mumbai
Become a Tech Industry Pioneer
CEH Course in Mumbai by Indian Cyber Security Solutions is your passport to becoming a cybersecurity champion. From grasping hacking fundamentals to mastering advanced penetration testing techniques, our CEH exam preparation course at ICSS covers the entire spectrum.
Experience genuine mentorship from seasoned professionals in the field. Our trainers are not just educators; they're mentors who guide you, share their experiences and help shape your path in the cybersecurity domain. Beyond education, we're committed to your success. Benefit from our job placement assistance, connecting you with potential employers and helping you kickstart your career in cybersecurity.
We firmly believe that cybersecurity education should be within reach for everyone and our course fees are competitively priced, ensuring that top-notch education is affordable. Your journey with ICSS doesn't end with the course completion. Enjoy ongoing support and access to updates, keeping you informed about the latest trends and advancements in the cybersecurity landscape.
With a commitment to accessible education, competitive pricing and a transformative learning approach, Indian Cyber Security Solutions is your trusted partner in the pursuit of cybersecurity excellence. Step into the world of cybersecurity confidently, knowing you have the support of a reliable friend and mentor in ICSS.
Best CEH Training Institute in Mumbai
Secure Your Future with Us
Best CEH Training Institute in Mumbai, Indian Cyber Security Solutions is your ultimate destination for top-quality ethical hacking education. We provide you with simple and efficient CEH test preparation training thanks to our adaptable learning alternatives and knowledgeable trainers that have successfully navigated real-world obstacles.
The field of cybersecurity is dynamic, with new threats emerging regularly. ICSS keeps its curriculum updated to reflect the latest developments in the cybersecurity landscape. Additionally, we conduct regular workshops and seminars to keep students informed about industry trends.
Positive reviews often mention the supportive and encouraging learning environment fostered by ICSS. Students appreciate the interactive nature of classes, where they feel comfortable asking questions and participating actively in discussions. This supportive atmosphere contributes to a positive overall learning experience. The success stories and positive feedback from past students speak volumes about the quality of training at ICSS.
ICSS provides dedicated placement assistance, including resume building, interview preparation, and connections to its extensive network of industry partners. This ensures that students are well-prepared for job opportunities after completing their CEH exam preparation training. Elevate your cybersecurity skills at Indian Cyber Security Solutions, recognized as the Best CEH Training Institute in Mumbai.
Course Eligibility
CEH Certification in Mumbai
Boost Your Career with Advanced Hacking Skills
CEH certification in Mumbai is a gateway to exciting global career prospects. This valued credential, recognized across diverse sectors like government, healthcare, technology, and finance, creates a high demand for CEH-certified professionals locally and internationally. With employers prioritizing these skills, achieving your CEH certification not only ensures job security but also opens doors for career advancement. It signifies to employers that you are prepared to tackle current and future cybersecurity challenges. If you aim for a career reaching beyond local boundaries onto a global scale, obtaining your CEH certification is the essential first step!
Get Started with FREE Demo Class:
*We don’t share your personal info with anyone.
Check out our Privacy Policy for more info.
Training Benefits
Course Module
Cover the fundamentals of key issues in the information security world, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Key topics covered:
Elements of Information Security, Cyber Kill Chain Methodology, MITRE ATT&CK Framework, Hacker Classes, Ethical Hacking, Information Assurance (IA), Risk Management, Incident Management, PCI DSS, HIPPA, SOX, GDPR
Learn how to use the latest techniques and tools to perform foot printing and reconnaissance, a critical pre-attack phase of the ethical hacking process
Hands-On Lab Exercises:
Over 30 hands-on exercises with real-life simulated targets to build skills on how to
- perform foot printing on the target network using search engines, web services, and social networking sites
- Perform website, email, whois, DNS, and network foot printing on the target network
Cover the fundamentals of key issues in the information security world, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Hands-On Lab Exercises:
Over 10 hands-on exercises with real-life simulated targets to build skills on how to
- Perform host, port, service, and OS discovery on the target network.
- Perform scanning on the target network beyond IDS and firewall.
Learn various enumeration techniques, such as Border Gateway Protocol (BGP) and Network File Sharing (NFS) exploits, plus associated countermeasures.
Hands-On Lab Exercises:
Over 20 hands-on exercises with real-life simulated targets to build skills on how to
Perform NetBIOS, SNMP, LDAP, NFS, DNS, SMTP, RPC, SMB, and FTP Enumeration
Learn how to identify security loopholes in a target organization’s network, communication infrastructure, and end systems.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform vulnerability research using vulnerability scoring systems and databases
- Perform vulnerability assessment using various vulnerability assessment tools
Learn about the various system hacking methodologies—including steganography, steganalysis attacks, and covering tracks—used to discover system and network vulnerabilities.
Hands-On Lab Exercises:
Over 25 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform Online active online attack to crack the system’s password
- Perform buffer overflow attack to gain access to a remote system
- Escalate privileges using privilege escalation tools
- Escalate privileges in linux machine
- Hide data using steganography
- Clear Windows and Linux machine logs using various utilities
- Hiding artifacts in Windows and Linux machines
Get an introduction to the different types of malware, such as Trojans, viruses, and worms, as well as system auditing for malware attacks, malware analysis, and countermeasures.
Hands-On Lab Exercises:
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Gain control over a victim machine using Trojan
- Infect the target system using a virus
- Perform static and dynamic malware analysis
Key topics covered:
Malware, Components of Malware, APT, Trojan, Types of Trojans, Exploit Kits, Virus, Virus Lifecycle, Types of Viruses, Ransomware, Computer Worms, Fileless Malware, Malware Analysis, Static Malware Analysis, Dynamic Malware Analysis, Virus Detection Methods, Trojan Analysis, Virus Analysis, Fileless Malware Analysis, Anti-Trojan Software, Antivirus Software, Fileless Malware Detection Tools
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Hands-On Lab Exercises:
Over 10 hands-on exercises with real-life simulated targets to build skills
- Perform MAC flooding, ARP poisoning, MITM and DHCP starvation attack
- Spoof a MAC address of Linux machine
- Perform network sniffing using various sniffing tools
- Detect ARP poisoning in a switch-based network
Key topics covered:
Network Sniffing, Wiretapping, MAC Flooding, DHCP Starvation Attack, ARP Spoofing Attack, ARP Poisoning, ARP Poisoning Tools, MAC Spoofing, STP Attack, DNS Poisoning, DNS Poisoning Tools, Sniffing Tools, Sniffer Detection Techniques, Promiscuous Detection Tools
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Hands-On Lab Exercises:
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
Perform social engineering using Various Techniques
Spoof a MAC address of a Linux machine
Detect a phishing attack
Audit an organization’s security for phishing attacks
Key topics covered:
Social Engineering, Types of Social Engineering, Phishing, Phishing Tools, Insider Threats/Insider Attacks, Identity Theft
Learn about different Denial-of-Service (DoS) and Distributed DoS (DDoS) attack techniques, as well as the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
Perform a DoS and DDoS attack on a target host
Detect and protect against DoS and DDoS attacks
Key topics covered:
DoS Attack, DDoS Attack, Botnets, DoS/DDoS Attack Techniques, DoS/DDoS Attack Tools, DoS/DDoS Attack Detection Techniques, DoS/DDoS Protection Tools
Understand the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Hands-On Lab Exercises:
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
Perform session hijacking using various tools
Detect session hijacking
Key topics covered:
Session Hijacking, Types of Session Hijacking, Spoofing, Application-Level Session Hijacking, Man-in-the-Browser Attack, Client-side Attacks, Session Replay Attacks, Session Fixation Attack, CRIME Attack, Network Level Session Hijacking, TCP/IP Hijacking, Session Hijacking Tools, Session Hijacking Detection Methods, Session Hijacking Prevention Tools
Get introduced to firewall, intrusion detection system, and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Hands-On Lab Exercises:
Over 7 hands-on exercises with real-life simulated targets to build skills on how to:
- Bypass Windows Firewall
- Bypass firewall rules using tunneling
- Bypass antivirus
Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
Hands-On Lab Exercises:
Over 8 hands-on exercises with real-life simulated targets to build skills on how to:
Perform web server reconnaissance using various tools
Enumerate web server information
Crack FTP credentials using a dictionary attack
Key topics covered:
Web Server Operations, Web Server Attacks, DNS Server Hijacking, Website Defacement, Web Cache Poisoning Attack, Web Server Attack Methodology, Web Server Attack Tools, Web Server Security Tools, Patch Management, Patch Management Tools
Learn about web application attacks, including a comprehensive web application hacking methodology used to audit vulnerabilities in web applications and countermeasures.
Hands-On Lab Exercises:
Over 15 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web application reconnaissance using various tools
- Perform web spidering
- Perform web application vulnerability scanning
- Perform a brute-force attack
- Perform Cross-Site Request Forgery (CSRF) Attack
- Identify XSS vulnerabilities in web applications
- Detect web application vulnerabilities using various web application security tools
Key topics covered:
Web Application Architecture, Web Application Threats, OWASP Top 10 Application Security Risks – 2021, Web Application Hacking Methodology, Web API, Webhooks, and Web Shell, Web API Hacking Methodology, Web Application Security
Learn about SQL injection attack techniques, injection detection tools, and countermeasures to detect and defend against SQL injection attempts.
Hands-On Lab Exercises:
Over 4 hands-on exercises with real-life simulated targets to build skills on how to
Perform an SQL injection attack against MSSQL to extract databases
Detect SQL injection vulnerabilities using various SQL injection detection tools
Key topics covered:
SQL Injection, Types of SQL injection, Blind SQL Injection, SQL Injection Methodology, SQL Injection Tools, Signature Evasion Techniques, SQL Injection Detection Tools
Learn about wireless encryption, wireless hacking methodologies and tools, and Wi-Fi security tools
Hands-On Lab Exercises:
Over 3 hands-on exercises with real-life simulated targets to build skills on how to:
Foot Print a wireless network
Perform wireless traffic analysis
Crack WEP, WPA, and WPA2 networks
Create a rogue access point to capture data packets
Key topics covered:
Wireless Terminology, Wireless Networks, Wireless Encryption, Wireless Threats, Wireless Hacking Methodology, Wi-Fi Encryption Cracking, WEP/WPA/WPA2 Cracking Tools, Bluetooth Hacking, Bluetooth Threats, Wi-Fi Security Auditing Tools, Bluetooth Security Tools
Learn about mobile platform attack vectors, Android vulnerability exploits, and mobile security guidelines and tools.
Hands-On Lab Exercises
Over 5 hands-on exercises with real-life simulated targets to build skills on how to
Hack an Android device by creating binary payloads
Exploit the Android platform through ADB
Hack an Android device by creating APK file
Secure Android devices using various Android security tools
Key topics covered:
Mobile Platform Attack Vectors, OWASP Top 10 Mobile Risks, App Sandboxing, SMS Phishing Attack (SMiShing), Android Rooting, Hacking Android Devices, Android Security Tools, Jailbreaking iOS, Hacking iOS Devices, iOS Device Security Tools, Mobile Device Management (MDM), OWASP Top 10 Mobile Controls, Mobile Security Tools.
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Hands-On Lab Exercises:
Over 2 hands-on exercises with real-life simulated targets to build skills on how to:
Gather information using Online foot printing tools
Capture and analyze IoT device traffic
Key topics covered:
IoT Architecture, IoT Communication Models, OWASP Top 10 IoT Threats, IoT Vulnerabilities, IoT Hacking Methodology, IoT Hacking Tools, IoT Security Tools, IT/OT Convergence (IIOT), ICS/SCADA, OT Vulnerabilities, OT Attacks, OT Hacking Methodology, OT Hacking Tools, OT Security Tools
Learn different cloud computing concepts, such as container technologies and server less computing, various cloud-based threats and attacks, and cloud security techniques and tools.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform S3 Bucket enumeration using various S3 bucket enumeration tools
- Exploit open S3 bucket
- Escalate IAM user privileges by exploiting misconfigured user policy
Key topics covered:
Cloud Computing, Types of Cloud Computing Services, Cloud Deployment Models, Fog and Edge Computing, Cloud Service Providers, Container, Docker, Kubernetes, Serverless Computing, OWASP Top 10 Cloud Security Risks, Container and Kubernetes Vulnerabilities, Cloud Attacks, Cloud Hacking, Cloud Network Security, Cloud Security Controls, Cloud Security Tools
In the final module, learn about cryptography and ciphers, public-key infrastructure, cryptography attacks, and cryptanalysis tools
Hands-On Lab Exercises:
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
Calculate MD5 hashes
Perform file and text message encryption
Create and use self-signed certificates
Perform email and disk encryption
Perform cryptanalysis using various cryptanalysis tools
Key topics covered:
Cryptography, Encryption Algorithms, MD5 and MD6 Hash Calculators, Cryptography Tools, Public Key Infrastructure (PKI), Email Encryption, Disk Encryption, Cryptanalysis, Cryptography Attacks, Key Stretching
Class Room Training
Fees: INR 15,000/- +18% GST
Training Duration: 3 Months
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Online Self Paced LIVE Training
Fees: INR 15,000/- +18% GST
Training Duration: 3 Months
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Listen from our students!
Trainers Details
- Indian Cyber Security Solutions (ICSS) trainers emphasize blended learning.
- Trainers at ICSS utilize real-life projects and case studies to provide practical knowledge of Ethical Hacking and Hackers.
- ICSS Ethical Hacking trainers in Bangalore have 12+ years of experience in the Networking field.
- Trainers at ICSS are working professionals from the cybersecurity field.
- ICSS trainers provide corporate training to enrich students' knowledge and industry-relevant skills.
- Regular assessments and individual attention are given to students for their progress.
- ICSS Ethical Hacking trainers assist students in resume building and develop their interpersonal skills.
Trainers Details
- Indian Cyber Security Solutions (ICSS) trainers emphasize blended learning.
- Trainers at ICSS utilize real-life projects and case studies to provide practical knowledge of Ethical Hacking and Hackers.
- ICSS Ethical Hacking trainers in Bangalore have 12+ years of experience in the Networking field.
- Trainers at ICSS are working professionals from the cybersecurity field.
- ICSS trainers provide corporate training to enrich students' knowledge and industry-relevant skills.
- Regular assessments and individual attention are given to students for their progress.
- ICSS Ethical Hacking trainers assist students in resume building and develop their interpersonal skills.
Frequently Asked Questions
What is the CEH (Certified Ethical Hacker) course?
One of the most coveted security certifications in the world is the Certified Ethical Hacker (CEH V12) designation. CEH stands for Certified Ethical Hacker. It is a professional certification that validates an individual's skills and knowledge in ethical hacking or penetration testing. Ethical hackers, also known as "white hat" hackers, use their expertise to identify vulnerabilities and weaknesses in computer systems, networks, and applications.
Why choose CEH exam preparation training at ICSS?
ICSS is well known for its experiential approach to CEH exam preparation training, which offers useful skills and real-world perspectives. Our curriculum is industry-aligned and our expert instructors make us the best option in Mumbai. Beyond training, ICSS provides comprehensive career support. This includes job placement assistance, internship opportunities and networking events, setting you on a path for a successful career in cybersecurity.
What are the prerequisites for CEH training at ICSS?
Basic understanding of networking and security concepts is beneficial, but our courses cater to both beginners and experienced professionals.
Is CEH training worth it?
Whether CEH training is worth it depends on your career goals and interests. If you're interested in cybersecurity and ethical hacking, CEH can provide valuable knowledge and a recognized certification. It may enhance your career opportunities in cybersecurity-related roles. However, it's essential to consider your own goals and the specific requirements of the industry or job you're interested in pursuing.
What is the salary of CEH fresher in India?
A competitive salary is to be expected in the cyber security industry. The average yearly wage for a CEH in India in 2023, per Glassdoor figures, will be $5,73,415. This conclusion highlights the market's need for knowledgeable personnel who can safeguard digital assets and reduce potential cyber dangers.
It's important to note that salaries can vary depending on your qualifications, certifications, experience, and the company you work for. Additionally, your earning potential is likely to increase as you obtain more expertise and knowledge in the field of ethical hacking. Due to the expanding importance of cyber security, there will be an increasing need for qualified people in this field, making it an exciting and worthwhile endeavor.
Is CEH certification worth it in India?
Yes, the CEH (Certified Ethical Hacker) certification is considered highly valuable in India. Here are several reasons why it is worth pursuing:
Industry Recognition: CEH is globally recognized and respected in the cybersecurity industry. Employers in India, as well as around the world, acknowledge and value this certification.
Skill Validation: CEH certification validates your skills in ethical hacking and cybersecurity. It demonstrates your proficiency in identifying vulnerabilities, assessing security measures, and conducting ethical hacking practices.
Career Opportunities: In India's rapidly growing digital landscape, the demand for skilled cybersecurity professionals is on the rise. Holding a CEH certification enhances your employability and opens doors to a wide range of career opportunities in various sectors.
Which institute is the best for CEH Exam Preparation Training?
When it comes to Certified Ethical Hacker (CEH) exam preparation training institutes in India, several alternatives offer first-class training and hands-on practical experience. Here are 5 renowned institutes, including ICSS, which is listed as the second alternative:
International Institute of Information Technology (IIIT Hyderabad):
IIIT Hyderabad offers comprehensive training programs in cybersecurity, including CEH. Their courses cover various aspects of network security, cryptography, and penetration testing.
Indian Cyber Security Solutions (ICSS):
ICSS is a leading institute in Hyderabad offering CEH exam preparation training. With industry experts as instructors, ICSS provides hands-on practical training in areas such as network security, web application security, and mobile app security.
EC-Council:
EC-Council is a globally recognized organization that offers CEH certifications. They provide comprehensive training through authorized training partners in Hyderabad, covering topics like penetration testing and vulnerability assessment.
Appin Technology Lab:
Appin Technology Lab offers specialized courses in cybersecurity, including CEH. Their training programs focus on practical skills and provide hands-on experience in real-world scenarios.
Institute of Information Security (IIS):
IIS offers a range of cybersecurity courses, including CEH training. Their programs emphasize practical training and cover topics such as network security, web application security, and wireless security.
Do ICSS Provide Placement Assistance?
ICSS is a cyber security company providing services to companies be it private and government agencies across the globe. The requirements come from the companies as we have strong contacts.
Can beginners enroll in CEH training at ICSS?
Absolutely! Our CEH exam preparation training programs at ICSS cater to both beginners and experienced professionals. The curriculum is designed to accommodate various skill levels, ensuring a comprehensive learning experience for all.
What If I Miss A Live Session?
Not a problem even if you miss a live session for some reason. If you are attending the LIVE classroom training at our office you can attend any of the parallel classes. Our Admin department is always available to solve any issues faced by students. However, for those attending the online class LIVE, these classes are being recorded and forwarded to all the students.
Achievements of our Students
Many of our students have founded Zero-Day Vulnerabilities and also their CVE has published on Exploit-DB. Check their CVE and also read their Blog on Exploit DB.
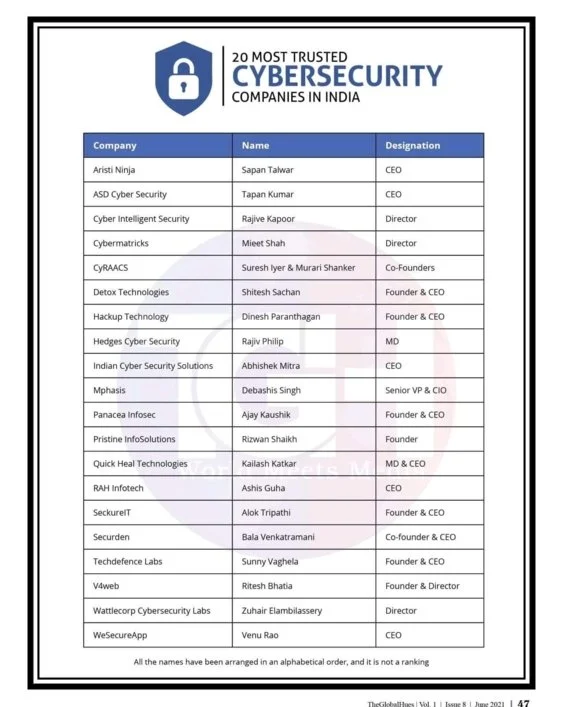
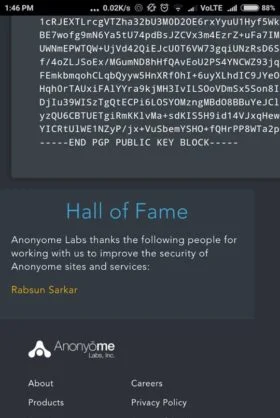
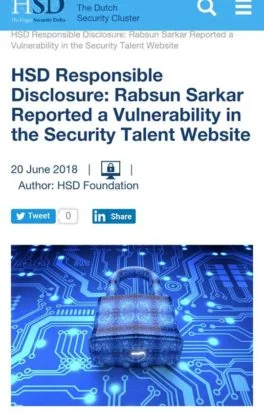
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
CEH Certification Training in Mumbai
CEH Certification Training in Mumbai helps you learn vital skills to protect our city's online world as things like banking and shopping become more digital. In Mumbai, known for its tech vibes, having these skills opens up cool job opportunities. Indian Cyber Security Solutions is here to guide you through this training, making sure your expertise is super valuable. Your job prospects in Mumbai's growing tech and cybersecurity scene can get a big boost with CEH certification.
Mumbai, with its diverse tech ecosystem, hosts numerous multinational IT companies and startups, creating a rising demand for skilled cybersecurity professionals. Cybersecurity consulting firms in Mumbai actively seek certified experts to deliver services that enhance the security posture of clients. Those with CEH certification in Mumbai can even explore entrepreneurship by providing cybersecurity consulting services or establishing their ventures.
At Indian Cyber Security Solutions, we go beyond just offering CEH exam preparation training; we guide you toward a future where your expertise is highly valued. With CEH certification, your employment prospects in Mumbai's thriving IT and cybersecurity industry can witness significant enhancement. Join us at Indian Cyber Security Solutions and let's embark on a journey to secure Mumbai's digital future together.

.webp)











































 (9).png)
 (18).png)
 (23).png)
.png)