CEH Training In Kolkata - C|EHv12 (Certified Ethical Hacker) Course from EC-Council

CEH Training in Kolkata is a global certification that is valid in more than 160 countries. We are an authorized training partner of the EC Council for the last 10 years. We have a pool of professional certified ethical hackers who are working as a security analyst in different organizations. CEH Ethical Hacking Certification in Kolkata from the EC council provides the gateway to enter the cybersecurity domain. MNCs have made CEH certification compulsory for the security-related jobs. Get the CEH Certification course in Kolkata from the Best CEH Training Institute in Kolkata, West Bengal.
There is numerous institute providing training on CEH Certification Course in Kolkata but ICSS is proud to be highest rated EC council training partner and Best CEH training institute in Kolkata, West Bengal which is highly popular because of our practical in-depth offensive hacking classes from penetration testers. Demand for CEH Certification course in Kolkata is at an all-time high.
This certification is highly important for security professionals. Someone may attack your system with malicious intentions, therefore your data fell prey to it. To save your organization from such intruders, skill yourself with CEH training in Kolkata.
Indian Cyber Security Solutions offers unique and comprehensive CEH v12 ethical training in Kolkata that provides you with the necessary skills to become a professional hacker. Our comprehensive curriculum includes topics including reverse engineering, writing code, and information infrastructure and management from databases. Under the guidance of industry experts with over 30 years of experience, students in our CEH v12 ethical hacking course in Kolkata, know concepts and learn effective solutions to combat malware threats and web servers to keep it safe. At Indian Cyber Security Solutions, we prioritize practical hands-on training and education. Through exposure to real-world scenarios and exercises, you will gain valuable experience in solving cyber security challenges. Our instructors offer in-depth knowledge and insight, ensuring you get the best education in ethical hacking.
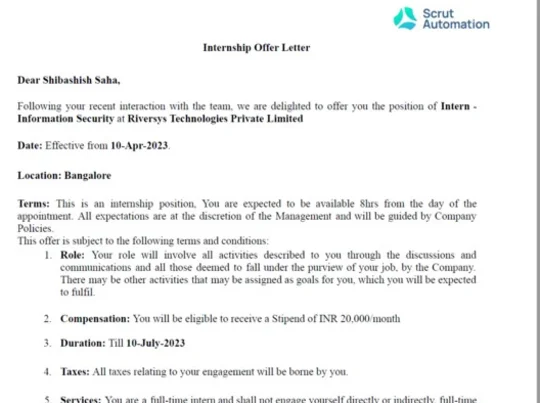
Congratulations to Shibashish Saha, a talented student of Indian Cyber Security Solutions, for securing an internship with a stipend of 20,000 INR per month!
We are thrilled to see Shibashish's hard work and dedication paying off, and we are proud to have played a part in his success.At Indian Cyber Security Solutions, we prioritize the growth and professional development of our students. We believe in providing them with real-world opportunities to apply their skills and knowledge. We do not engage in fake placements or internships. The screen shots displayed are proof of Shibashish's accomplishment and our commitment to genuine career opportunities. Shibashish's achievement is a testament to the quality of our training programs and the expertise of our instructors. Indian Cyber Security Solutions has proven track record of placing 90% of students who have completed the CEHv12 training in kolkata.
We strive to equip our students with the practical skills and industry insights needed to excel in the field of cyber security and ethical hacking training in Kolkata. We congratulate Shibashish once again on his well-deserved internship and wish him all the best in this new chapter of his professional journey. We are confident that he will make a significant impact and gain valuable experience during his internship.At Indian Cyber Security Solutions, we remain committed to providing our students with the best education, genuine placement opportunities, and a solid foundation for a successful career in cyber security. We take pride in our students' achievements and look forward to witnessing many more success stories in the future.If you are looking to kick start your career in cyber security, trust Indian Cyber Security Solutions to provide you with the knowledge, skills, and real-world opportunities to thrive. Join us today and unlock your potential in the dynamic field of cyber security.
4.9 ( 21,123 ratings )
1,09,233 Students Enrolled
- Our Kolkata Office
- Our Bangalore Office
The secret behind our achievements and awards is when you enroll in our Ethical Hacking course, you will gain knowledge in important areas such as vulnerability analysis, network security, penetration testing etc. We focus on empowering you with the skills needed to find out and effectively mitigate cyber threats. Join Indian Cyber Security Solutions today and start your journey to become a skilled and ethical hacker. Our course is designed to meet industry standards and prepare you for a successful career in the cyber security industry. Don’t miss this opportunity to improve your skills and knowledge. Register now Unlock your power in active ethical hacking with Indian Cyber Security Solutions.

Ethical Hacking Course in Kolkata by one of the best ethical hacking training institute in Bangalore, Indian Cyber Security Solutions is INR 15000 only (Certified Ethical Hacking Professional – CEHP). This ethical hacking training course is available both online and in classroom training mode.
It can take anywhere from a few months to a few years to become an ethical hacker, depending on your level of experience and expertise. For those just starting out, you can enroll for CEHP course by Indian Cyber Security Solutions which will only take 3 months. ICSS even offers 100% placement assistance.
The average salary for a certified Ethical Hacker is ₹5,21,271 per year in Kolkata. Indian Cyber Security Solutions have mentored students who got placed at a higher package because of their industry best trainers with 10+ of experience.
CEHP provided by Indian Cyber Security Solutions is a 3 months certification course where anyone with a Bachelor's degree (BSc, BTech, BE, BCA, even BA or BCom students) to become an ethical hacker. Candidates having an advanced diploma in network security can also opt for ethical hacking as a career. Even after 12th they can go for Diploma in Cyber Security provided by ICSS.
Certified Ethical Hacking Professional by Indian Cyber Security Solutions is the best certificate course for ethical hacking due to their experienced trainers and low cost. ICSS have trained over 5000 students over the years and 500+ students have been placed in the industry.
C|EH v12 – Certified Ethical Hacker from EC-Council
A Certified Ethical Hacker holds the reins of network and system security tightly in his hands. CEH v12 is the latest addition to this certification. The extensive practical training provided by CEH training in Kolkata equips live projects and simulations. CEH course in Kolkata by ICSS is among the best in India with around 1298+ students acquiring CEH certification from ICSS are placed in different companies across the globe.
CEH training in Kolkata with hands-on training in the lab from the professional hackers who are themselves CEHv12 certified, OSCP Certified. Cyber Security training is in huge demand as organizations are going online with more than 170 Billion Dollar investment in the cyber security domain worldwide. At Indian Cyber Security Solutions, you will learn in-depth on an attacker can hack an organization and also how the defend the intellectual property of the organization from being hacked. CEH training in Kolkata is designed is such a way that you get the maximum practical knowledge. At our training center, we bring in guest faculties from the industry so they can share their practical experience with you. At the end of the course, we aim to make your placement ready.
Indian Cyber Security Solutions have 130+ trainers who are professional Ethical Hackers working in different MNCs like Infosys, Cognizant, Wipro, ATOS, Intel and are also members of our research & development team. All the trainers are geographically located in different areas provide online training on Ethical Hacking. All the CEH v12 training classes are held through an application where the faculty and the students are LIVE interacting with each other over the internet. All the classes are recorded and uploaded in our online portal “ HACKERS LAB “ where all students have lifetime access. We guarantee your satisfaction or we pay back your course fee. There will be 3 instructors dedicated to individual batch which will carry on for 3 months
Eligibility Criteria to become a Professional Ethical Hacker
The prime objective of this course is to make you ready for the industry where you can use your skills to protect the organization. After completion of this course, you will be able to successfully document the Vulnerability Assessment report for the organization.
Tools that will be covered by Indian Cyber Security Solutions
RECENT PLACEMENTS RECORDS
Shaik Chinnu got placed at Abhibus as a Cyber Security Analyst
Anirban Sasmal got placed at Intlum Technology Pvt. Ltd. as an Android Application Developer
Prabhu Kalyan Samal got placed at TCS as a Computer Consultancy
Simul Dey got placed at Wipro as a Network Administrator
Unleash Your Potential with CEHv12 Certification in Kolkata: Comprehensive Training, Real-World Experience, and Internship Opportunity
Looking to get CEHv12 certification in Kolkata? Look no further! Indian Cyber Security Solutions (ICSS) Kolkata offers comprehensive CEHv12 training that prepares you for the Certified Ethical Hacker Version 12 certification exam. Our course covers two popular tools used in ethical hacking, ensuring you have a all round understanding of the subject. At ICSS, we believe in practical training and real-world applications.
Throughout the course you will gain hands-on experience with various open source tools such as Metasploit, Wireshark, Nmap, and more. These tools are widely used in the industry and will give you the skills you need to successfully perform ethical hacking. A unique feature of our CEHv12 training in Kolkata is our focus on VAPT (Vulnerability Assessment and Penetration Testing).
You will learn how to prepare detailed reports and documents, which are critical for investigating vulnerabilities and presenting findings to stakeholders. On completion of the course you will have the opportunity to start your career with a three months internship with ICSS.
During the internship you will work on live VAPT projects, gaining invaluable real-world experience under the guidance of industry experts. Earning CEHv12 certification opens up a wide range of career opportunities in cyber security. With ICSS’s comprehensive training, strategic approach and career opportunities, you will be well prepared to excel in your future endeavours. Enroll in CEHv12 training at ICSS today and take the first steps to becoming a certified ethical hacker. Gain hands-on experience with open source and popular tools, knowledge of VAPT documentation, and gain valuable business opportunities. Don’t leave you
Listen from our students!
Learn from Industry Experts & Get Real Hands-On Experience and get job ready
- 100% Placement Support After completion course
- Practice on Real Time Projects which can be showcased to future recruiters
- Learn from industry experts who have over 12+ Years Industry Experience
- Demand for Ethical Hacking & Cyber Security will increase to 80% by 2022
- Top Companies Hiring: Google, Facebook, Amazon, Apple, Uber & Many More.
- Advanced Course Curriculum
- 1500+ Professionals Trained with 4.8/5 Rating
Learn from Industry Experts & Get Real Hands-On Experience and get job ready

Get Started with FREE Demo Class:
* We don’t share your personal info with anyone. Check out our Privacy Policy for more info.
Why You Should Choose ICSS ?
Industry professions from Amazon, Cognizant & Intel will share their practical experience in the class
100% practical and lab-based classes (available online & offline)
25% Scholarship program for merited students with a minimum of 95% & above marks in their 12th board exams.
LIFETIME access to video tutorials, case studies
EMI option is available if you go for 2 or more courses.
Get educational loan @ O% interest
JOB ORIENTED ETHICAL HACKING COURSE DETAILS
100% Job Placement Assistance
- Career Guide: Job Opportunities will be shared with you
- Be JOB Ready Resume prepared by Experts
- Questions & Answers provided for interviews
- Mock Exams you will write to test your skills
- Mock Interviews to boost your confidence
- Pre-Requisite: Any one can learn Ethical Hacking and Get Job
- Projects: You work on Real Life Case Studies
Course Duration
We Provide:
- 40 Hours Classes
- Fast Track Classes
- Weekdays & Weekend Classes
In Class, You Get In-Depth ethical hacking Knowledge on each topic
- Projects to do assignments
- Location: Courses are run in our Kolkata training center (Salt Lake, Sector 5) & Bangalore (Indiranagar)
- Corporate Training for your Employees
- Online Ethical Hacking CEH v12 Courses - Live Instructor LED Classes
- Pay only after attending FREE DEMO CLASS
C|EH v12 - Course Module
Cover the fundamentals of key issues in the information security world, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Key topics covered:
Elements of Information Security, Cyber Kill Chain Methodology, MITRE ATT&CK Framework, Hacker Classes, Ethical Hacking, Information Assurance (IA), Risk Management, Incident Management, PCI DSS, HIPPA, SOX, GDPR
Learn how to use the latest techniques and tools to perform foot printing and reconnaissance, a critical pre-attack phase of the ethical hacking process.
Hands-On Lab Exercises:
Over 30 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform foot printing on the target network using search engines, web services, and social networking sites
- Perform website, email, whois, DNS, and network foot printing on the target network
Cover the fundamentals of key issues in the information security world, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Hands-On Lab Exercises:
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform host, port, service, and OS discovery on the target network
- Perform scanning on the target network beyond IDS and firewall
Learn various enumeration techniques, such as Border Gateway Protocol (BGP) and Network File Sharing (NFS) exploits, plus associated countermeasures.
Hands-On Lab Exercises:
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform NetBIOS, SNMP, LDAP, NFS, DNS, SMTP, RPC, SMB, and FTP Enumeration
Learn how to identify security loopholes in a target organization’s network, communication infrastructure, and end systems.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform vulnerability research using vulnerability scoring systems and databases
- Perform vulnerability assessment using various vulnerability assessment tools
Learn about the various system hacking methodologies—including steganography, steganalysis attacks, and covering tracks—used to discover system and network vulnerabilities.
Hands-On Lab Exercises:
Over 25 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform Online active online attack to crack the system’s password
- Perform buffer overflow attack to gain access to a remote system
- Escalate privileges using privilege escalation tools
- Escalate privileges in linux machine
- Hide data using steganography
- Clear Windows and Linux machine logs using various utilities
- Hiding artifacts in Windows and Linux machines
Get an introduction to the different types of malware, such as Trojans, viruses, and worms, as well as system auditing for malware attacks, malware analysis, and countermeasures.
Hands-On Lab Exercises:
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Gain control over a victim machine using Trojan
- Infect the target system using a virus
- Perform static and dynamic malware analysis
Key topics covered:
Malware, Components of Malware, APT, Trojan, Types of Trojans, Exploit Kits, Virus, Virus Lifecycle, Types of Viruses, Ransomware, Computer Worms, Fileless Malware, Malware Analysis, Static Malware Analysis, Dynamic Malware Analysis, Virus Detection Methods, Trojan Analysis, Virus Analysis, Fileless Malware Analysis, Anti-Trojan Software, Antivirus Software, Fileless Malware Detection Tools
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Hands-On Lab Exercises:
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform MAC flooding, ARP poisoning, MITM and DHCP starvation attack
- Spoof a MAC address of Linux machine
- Perform network sniffing using various sniffing tools
- Detect ARP poisoning in a switch-based network
Key topics covered:
Network Sniffing, Wiretapping, MAC Flooding, DHCP Starvation Attack, ARP Spoofing Attack, ARP Poisoning, ARP Poisoning Tools, MAC Spoofing, STP Attack, DNS Poisoning, DNS Poisoning Tools, Sniffing Tools, Sniffer Detection Techniques, Promiscuous Detection Tools
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Hands-On Lab Exercises:
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform social engineering using Various Techniques
- Spoof a MAC address of a Linux machine
- Detect a phishing attack
- Audit an organization’s security for phishing attacks
Key topics covered:
Social Engineering, Types of Social Engineering, Phishing, Phishing Tools, Insider Threats/Insider Attacks, Identity Theft
Learn about different Denial-of-Service (DoS) and Distributed DoS (DDoS) attack techniques, as well as the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform a DoS and DDoS attack on a target host
- Detect and protect against DoS and DDoS attacks
Key topics covered:
DoS Attack, DDoS Attack, Botnets, DoS/DDoS Attack Techniques, DoS/DDoS Attack Tools, DoS/DDoS Attack Detection Techniques, DoS/DDoS Protection Tools
Understand the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Hands-On Lab Exercises:
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform session hijacking using various tools
- Detect session hijacking
Key topics covered:
Session Hijacking, Types of Session Hijacking, Spoofing, Application-Level Session Hijacking, Man-in-the-Browser Attack, Client-side Attacks, Session Replay Attacks, Session Fixation Attack, CRIME Attack, Network Level Session Hijacking, TCP/IP Hijacking, Session Hijacking Tools, Session Hijacking Detection Methods, Session Hijacking Prevention Tools
Get introduced to firewall, intrusion detection system, and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Hands-On Lab Exercises:
Over 7 hands-on exercises with real-life simulated targets to build skills on how to:
- Bypass Windows Firewall
- Bypass firewall rules using tunneling
- Bypass antivirus
Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
Hands-On Lab Exercises:
Over 8 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web server reconnaissance using various tools
- Enumerate web server information
- Crack FTP credentials using a dictionary attack
Key topics covered:
Web Server Operations, Web Server Attacks, DNS Server Hijacking, Website Defacement, Web Cache Poisoning Attack, Web Server Attack Methodology, Web Server Attack Tools, Web Server Security Tools, Patch Management, Patch Management Tools
Learn about web application attacks, including a comprehensive web application hacking methodology used to audit vulnerabilities in web applications and countermeasures.
Hands-On Lab Exercises:
Over 15 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web application reconnaissance using various tools
- Perform web spidering
- Perform web application vulnerability scanning
- Perform a brute-force attack
- Perform Cross-Site Request Forgery (CSRF) Attack
- Identify XSS vulnerabilities in web applications
- Detect web application vulnerabilities using various web application security tools
Key topics covered:
Web Application Architecture, Web Application Threats, OWASP Top 10 Application Security Risks – 2021, Web Application Hacking Methodology, Web API, Webhooks, and Web Shell, Web API Hacking Methodology, Web Application Security
Learn about SQL injection attack techniques, injection detection tools, and countermeasures to detect and defend against SQL injection attempts.
Hands-On Lab Exercises:
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform an SQL injection attack against MSSQL to extract databases
- Detect SQL injection vulnerabilities using various SQL injection detection tools
Key topics covered:
SQL Injection, Types of SQL injection, Blind SQL Injection, SQL Injection Methodology, SQL Injection Tools, Signature Evasion Techniques, SQL Injection Detection Tools
Learn about wireless encryption, wireless hacking methodologies and tools, and Wi-Fi security tools
Hands-On Lab Exercises:
Over 3 hands-on exercises with real-life simulated targets to build skills on how to:
- Foot Print a wireless network
- Perform wireless traffic analysis
- Crack WEP, WPA, and WPA2 networks
- Create a rogue access point to capture data packets
Key topics covered:
Wireless Terminology, Wireless Networks, Wireless Encryption, Wireless Threats, Wireless Hacking Methodology, Wi-Fi Encryption Cracking, WEP/WPA/WPA2 Cracking Tools, Bluetooth Hacking, Bluetooth Threats, Wi-Fi Security Auditing Tools, Bluetooth Security Tools
Learn about mobile platform attack vectors, Android vulnerability exploits, and mobile security guidelines and tools.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Hack an Android device by creating binary payloads
- Exploit the Android platform through ADB
- Hack an Android device by creating APK file
- Secure Android devices using various Android security tools
Key topics covered:
Mobile Platform Attack Vectors, OWASP Top 10 Mobile Risks, App Sandboxing, SMS Phishing Attack (SMiShing), Android Rooting, Hacking Android Devices, Android Security Tools, Jailbreaking iOS, Hacking iOS Devices, iOS Device Security Tools, Mobile Device Management (MDM), OWASP Top 10 Mobile Controls, Mobile Security Tools.
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Hands-On Lab Exercises:
Over 2 hands-on exercises with real-life simulated targets to build skills on how to:
- Gather information using Online foot printing tools
- Capture and analyze IoT device traffic
Key topics covered:
IoT Architecture, IoT Communication Models, OWASP Top 10 IoT Threats, IoT Vulnerabilities, IoT Hacking Methodology, IoT Hacking Tools, IoT Security Tools, IT/OT Convergence (IIOT), ICS/SCADA, OT Vulnerabilities, OT Attacks, OT Hacking Methodology, OT Hacking Tools, OT Security Tools
Learn different cloud computing concepts, such as container technologies and server less computing, various cloud-based threats and attacks, and cloud security techniques and tools.
Hands-On Lab Exercises:
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform S3 Bucket enumeration using various S3 bucket enumeration tools
- Exploit open S3 buckets
- Escalate IAM user privileges by exploiting misconfigured user policy
Key topics covered:
Cloud Computing, Types of Cloud Computing Services, Cloud Deployment Models, Fog and Edge Computing, Cloud Service Providers, Container, Docker, Kubernetes, Serverless Computing, OWASP Top 10 Cloud Security Risks, Container and Kubernetes Vulnerabilities, Cloud Attacks, Cloud Hacking, Cloud Network Security, Cloud Security Controls, Cloud Security Tools
In the final module, learn about cryptography and ciphers, public-key infrastructure, cryptography attacks, and cryptanalysis tools.
Hands-On Lab Exercises:
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Calculate MD5 hashes
- Perform file and text message encryption
- Create and use self-signed certificates
- Perform email and disk encryption
- Perform cryptanalysis using various cryptanalysis tools
Key topics covered:
Cryptography, Encryption Algorithms, MD5 and MD6 Hash Calculators, Cryptography Tools, Public Key Infrastructure (PKI), Email Encryption, Disk Encryption, Cryptanalysis, Cryptography Attacks, Key Stretching

Class Room Training
3 Months Training
2 Classes Per Week X 2 Hours Each Day
Week End Classes | Week Days Classes
Online Self Paced LIVE Training
3 Months Training
2 Classes Per Week X 2 Hours Each Day
Week End Classes | Week Days Classes
Achievements of our Students
Many of our students have founded Zero-Day Vulnerabilities and also their CVE has published on Exploit-DB. Check their CVE and also read their Blog on Exploit DB.
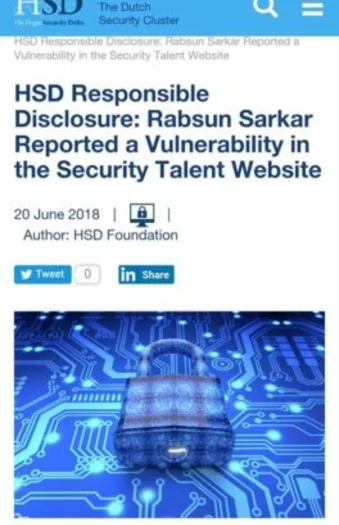
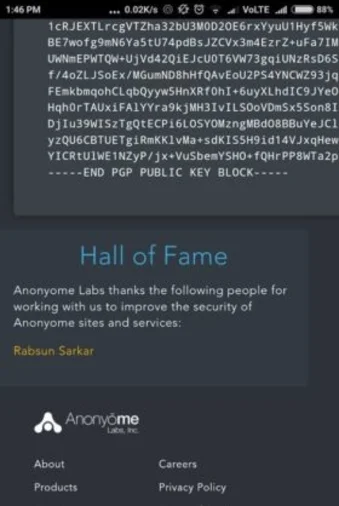
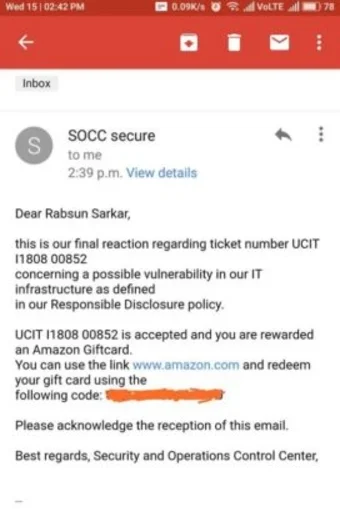
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
CEH Course in Kolkata from ICSS with 100% placement assistance
CEH Course in Kolkata by Indian Cyber Security Solutions is the most demanded CEH training in Kolkata as well as in India. More than 1000+ student placed in different company after CEH Course in Kolkata. This city attracts millions of IT professional to keep the IT dream alive. So it is great opportunity to all Kolkata students. You are on the right track if you are thinking of doing a CEH Training in Kolkata as some of the most promising Indian start-ups and the biggest companies of the world have offices in this city.
Today, companies across the world are struggling with the issue of data and network security. CEH Course in Kolkata will prepare you for security professional to work as an Ethical Hacker and Penetration Tester. This course confirms the capacities of an ethical hacker to prepare for vulnerabilities of system foundation and prevent illegal hacking. The most ideal approach to do this is by understanding the strategies utilized by hackers to interfere into systems.
CEH from EC-Council is one of the most demanding course for IT security specialists, especially for those, who are looking for job prospects in penetration testing. In spite of the fact that the certification is must be required for entrance analyzers and its focal points are not limited.
This Course acts as the foundation stone in your career to be a Penetration Tester and providing security to networks and websites. Hacking is a technique by which a person can bypass system’s defence. Ethical Hackers use the same technique instead of taking advantage of any vulnerabilities that are found they document them and provide actionable advice on how to fix them. The purpose of ethical hacking is to evaluate the security of and identify vulnerabilities in systems, networks or system infrastructure.
Need to Work on real-time projects and complete assignments to get Professional Certification from Indian Cyber Security Solutions
ICSS provides the course completion certificate once you successfully complete the Certified Ethical Hacking training program Professional Certificate Holders work at 1000s of companies like HP, TCS, Amazon, Accenture and many more.
REGISTRATION DESK

Current Job Openings
Check job profile, salary scale of current jobs available in market
CEH Certification Course in Kolkata is what students & working professionals are looking for career opportunity in the cyber security field
CEH Certification Course in Kolkata offers 100% placement assistance to our students for a corporate career. Today’s digital era, one of the biggest threats comes from cybercriminals. Hackers were not taken seriously until a few years back. In addition, some big names in the Indian industry had to pay a large amount of money to hackers. So that they keep the information confidential. According to surveys guided by cybersecurity firms in the country, Indian firms lost more than $4 billion in 2013 alone because of hackers. Our trainers are not just trainers, they are Industry Experts. You will get hands-on training during CEH Certification Course in Kolkata. CEH Certification Course in Kolkata is a highly-valued certification. You will be able to get the desired job in this field. Ethical hackers work as information security professionals and are considered notable in all information technology zones. Certified Ethical Hackers keep a check on security issues related to Information Security. Ethical Hackers are hired by all organizations those who have critical business data online.
What does an organization expect from a Cyber Security Professional?
Our training module is delicately balanced between practical lab based training and theoretical content. Organizations expect real time practical based solutions to the real world threat of cyber attack. Focusing on practical training conducted by Bug Bounty hunters and exploit writers. ICSS CEH Certification Course in Kolkata will surely give you the edge and help you to grab the job. Our ceh program also focuses on the most important aspect of “Documentation” / “VAPT Reporting”. Cyber security professionals will not only impart you with latest cyber security training but will also help you to prepare and report critical vulnerabilities to companies as a bug bounty hunter and also helps you in VAPT report writing. For an organization a cyber security professional who has technical and as well as reporting / documentation skill will always be the first choice. This reduces the investment of organizations on the newly recruited cyber security professional. There is a huge demand for ethical hackers and the CEH Certification Course in Kolkata.
So you can take help to brighten your job prospects in some of the biggest global companies in the world. The CEH Training in Kolkata is a new credential in the IT certification industry, but its importance and influence have grown quickly. Indian Cyber Security Solutions is proud to be the highest rated CEH certification training institute in Kolkata with around 1890+ students taking admission every year across the globe. CEH Certification Course in Kolkata is highly demanded as all companies whether big or small require cybersecurity professionals to prevent data breaches. Individual students who opt for CEH Certification Course in Kolkata could expect a minimum of 3.0 Lakh package salary as fresher’s around the globe.
Best CEH Training Institute in Kolkata, WestBengal
Best CEH Training Institute in Kolkata, WestBengal Indian Cyber Security Solutions will give you vast knowledge about hacking. Ethical hackers use their skills and many of the same methods and techniques to test and bypass organizations’ IT security as their unethical counterparts, who are referred to as black hat hackers. The trainers are industry professionals. They work in many projects. Becoming Ethical hackers you can find security exposures in insecure system configurations, known and unknown hardware or software vulnerabilities as well as operational weaknesses in process or technical countermeasures.
The Ethical hackers help companies determine which of their IT security measures are effective, which need to be updated and which contain vulnerabilities that can be exploited. When ethical hackers finish evaluating organizations’ systems, they report back to company leaders about those vulnerable areas, for instance, a lack of sufficient password encryption, insecure applications or exposed systems running un-patched software. Cyber attacks can cripple or destroy a business, especially a small business. However, most companies are completely unprepared for cyber attacks.
Ethical hackers understand how threat actors operate and they know how these bad actors will use new information and techniques to attack systems. You will learn all these things from ICSS,
Best CEH Training Institute in Kolkata, Karnataka. After CEH Training in Kolkata you can the hacking skills to protect any organizations’ website. However if you want to join an institute for learning Ethical hacking then you can join ICSS, Best CEH Training Institute in Kolkata, Karnataka. Ethical hackers generally use the same hacking skills that malicious actors use to attack enterprises. Ethical Hacking has been a lucrative career option for many, and not without good reason! It’s a challenging job that never gets boring, pays well and also brings a greater sense of achievement.
Indian Cyber Security Solutions offers the best CEH training as they are the Best CEH Training Institute in West Bengal. We focus on in-depth knowledge of the learners through our experts. Therefore, you will able to improve your knowledge of risks and vulnerabilities. At first, you have to think like a hacker to learn ethical hacking. Best CEH Training Institute in West Bengal delivers a 90% practical course by penetration testers who are themselves CEH certified and OSCP certified. Indian Cyber Security Solutions is located in salt lake sector 5 Kolkata. It is surrounded by MNC’s. Branches of renowned IT companies like Accenture, IBM, Tech Mahindra, Technologies, and Lexmark are located in salt lake sector V Kolkata, near our corporate office of sector V. The location is the best choice for professionals including business travelers. Along with CEH Training in Kolkata, we provide placement assistance to the students as we are the Best CEH Training Institute in West Bengal. 20 + certified ethical hackers will be your trainer for 2 months. Apart from a certification exam conducted by EC- council at the end of the course we make sure you be well prepared at the Best CEH Training Institute in West Bengal. Cybersecurity professionals will guide you with the best practical knowledge to be a successful CEH v11 certified ethical hacker.
Still Hunting for a Job? or Want to Make a Career Switch into
Cyber Security?
Recruiters are looking for you!
All you need to Learn Basic to Advance of CEH with ICSS, Become Certified Professional and Get JOB with our Free Placement Assistance Program
Benefits of completing Ethical Hacking Training in Kolkata by Indian Cyber Security Solutions
The CEHP course by ICSS provides hands-on training in ethical hacking and information security, making you job-ready. It covers the latest tools, techniques, and techniques in the industry. With a certification from ICSS, you can confidently apply for ethical hacking and information security roles in MNCs.
CITI Group: CITI Group is recruiting Information Security Professionals, and to meet the eligibility requirements, CEHP certification is required. ICSS offers CEHP certification courses that can help professionals prepare for this role. It covers all important aspects of cybersecurity, from threats to countermeasures, and ensures candidates are fully equipped to address information security challenges. The average CTC as per Glassdoor is INR 11.50 LPA.
Deutsche Bank: Deutsche Bank Hires Information Security Professional professionals. The ICSS Certified Ethical Hacking Professional (CEHP) course can help candidates develop the skills necessary to apply for this position. The course provides hands-on training to identify vulnerabilities and protect against cyber threats, qualifying candidates for careers in information security. The average CTC as per Glassdoor is between INR 11-11.70 LPA.
ORACLE: Oracle is hiring computer forensics engineers, Network Security Engineers to enhance its cybersecurity capabilities. The ICSS-provided CEHP course can help individuals develop the skills necessary to qualify for this role and excel in electronic forensic investigations. The average CTC as per Glassdoor is between INR 8-26 LPA.Intel: Intel is hiring computer forensics engineers to help identify, investigate, and prevent cyber threats. ICSS’s CEHP course can help individuals gain the necessary skills and complete advanced CHFI courses to secure such roles by providing them with knowledge in cyber forensics, incident response, and malware analysis.
Deloitte: Deloitte is hiring ethical hackers with salary up to INR 10-12 LPA. The ICSS CEHP course can help candidates improve their skills in ethical hacking and cybersecurity, increasing their chances of getting a job with Deloitte. Enroll in the ICSS CEHP course today and start your career in cyber security.
Accenture: Accenture is hiring ethical hackers with an average salary of ₹9,00,000 per annum. The ICSS CEHP course can help individuals gain the necessary skills to become ethical hackers and get a job with companies like Accenture. Join ICSS and take your first step toward a successful career in cybersecurity.
IBM: IBM hires Network Security Engineers with an average salary of INR 7-9.75 LPA. The ICSS CEHP course can help individuals develop the skills necessary to secure computer networks and prevent unauthorized access. Join ICSS and start your career in Network Security Engineering at IBM.
CISCO: Cisco Systems is hiring Network Security Engineers with salaries ranging from INR 7-10 LPA. Indian Cyber Security Solutions’ CEHP course provides hands-on training and certification in network security, equipping candidates with the knowledge and skills required for a career in this field.
Cyber Security Course in Kolkata
Cyber security course in Kolkata and workshops are conducted across all collages. ICSS had been fortunate enough to have been associated with some of the renounced educational institutions like IIT Kharagpur, NIT Durgapur, Jadavpur University, Lovely Professional University and JIS collage to name a few. Our campus representatives are highly active and conduct interactive sessions on cyber security. Campus representatives are student’s representatives from different collages those who are responsible for establishing a research lab on cyber security inside the campus of the respective collages. These research facilities & interactive sessions on ethical hacking helps the students to gain latest knowledge in cyber security. Indian Cyber Security Solutions offers Cyber security course in Kolkata for corporate teams and individuals.
How you can get priority in Job Placement after doing the course from ICSS?
There is no better time than now to begin a career in the cybersecurity industry. In fact, candidates who will accomplish a CEH Ethical Hacking Certification in Kolkata can get career opportunities with high pay scales. Indian Cyber Security Solutions had trained more than 1298+ students and is proud to be the best CEH Ethical Hacking Certification in Kolkata. With around 20+ penetration testers and ethical hackers working with Indian Cyber Security Solutions, it is quite easy to provide world-class practical training which is required for CEH certification. CEH Ethical Hacking Certification in Kolkata. You will be able to improve your knowledge of risks and vulnerabilities and learn how to think like a hacker.
After that course, it will boost your salary and advance your security career. You will learn to use the real hacking tool. Cybercriminals are innovators and will constantly discover new ways to attack IT infrastructure and exploit vulnerabilities. Without knowledge of the risks and vulnerabilities associated with your computer systems, you will have a difficult time keeping them secure. ICSS confirms by their course of CEH Ethical Hacking Certification in Kolkata the capacities of an ethical hacker to prepare for vulnerabilities of system foundation and prevent illegal hacking.
Do you want to be a Campus Representative?
If you want to be a CR there is a long list of benefits that you will be entitled too.