CEH Training in Chandigarh –
C|EH v 11 (Certified Ethical Hacker) Course
CEH training in Chandigarh with practical certification course from EC council. Best CEH training institute in Chandigarh with hands on practical LIVE classes on Kali Linux, Metasploit. After attending CEH course in Chandigarh students will be capable in finding out vulnerabilities in Website, Network, Android Applications and IOS applications. CEH Course in Chandigarh is in huge demand as professionals are looking to grab the opportunity as the industry demands rises.
CEH training in Chandigarh by Indian Cyber Security Solutions is a great opportunity for the people of Chandigarh. They can reach in higher position as a Cyber Security professional. Chandigarh Is World’s 2nd Fastest Growing Startup Ecosystem.
Chandigarh has risen four places in the latest Global Startup Ecosystem Ranking by San Francisco-based Compass. The ethical hacker is a trusted person who has appointed to provide guard against hacking attempts.
4.8 ( 21,123 ratings )
1,09,233 Students Enrolled
C|EH v11 – Certified Ethical Hacker - EC Council Certification
There is a worldwide demand for information security professionals these days. Chandigarh a one-stop destination for a huge number of jobs and career opportunities. Also many IT companies will develop in Chandigarh in the upcoming future. You will get deep hands on practical knowledge from real ethical hackers. Our trainers are working as an ethical hacker. Join Indian Cyber Security Solutions for CEH training in Chandigarh.
CEH Training in Chandigarh will help you to enter the cyber security domain. CEH course will help Chandigarh students to enter the cyber security domain. Chandigarh is the third-most-populous city in India and it attracts entrepreneurs, startups, tech experts, etc. Chandigarh has one of the most highly educated workforces in the world.
CEH training in Chandigarh with hands-on training in the lab from the professional hackers who are themselves CEHv11 certified, OSCP Certified. Cyber Security training is in huge demand as organizations are going online with more than 170 Billion Dollar investment in the cyber security domain worldwide. At Indian Cyber Security Solutions, you will learn in-depth on an attacker can hack an organization and also how the defend the intellectual property of the organization from being hacked. CEH v11 training is designed is such a way that you get the maximum practical knowledge. At our training center, we bring in guest faculties from the industry so they can share their practical experience with you. At the end of the course, we aim to make your placement ready.
Indian Cyber Security Solutions have 130+ trainers who are professional Certified Ethical Hackers working in different MNCs like Infosys, Cognizant, Wipro, ATOS, Intel and are also members of our research & development team. All the trainers are geographically located in different areas provide online training on Ethical Hacking. All the CEH v11 training classes are held through an application where the faculty and the students are LIVE interacting with each other over the internet. All the classes are recorded and uploaded in our online portal “ HACKERS LAB “ where all students have lifetime access. We guarantee your satisfaction or we pay back your course fee. There will be 3 instructors dedicated to individual batch which will carry on for 3 months.
Eligibility Criteria to become a Certified Ethical Hacker certified from EC-Council
The prime objective of this course is to make you ready for the industry where you can use your skills. After completion of CEH training in Chandigarh, you will be able to successfully create AI tools by using machine learning. Any graduate with knowledge of basic programming languages can apply for this course.
If you had completed your graduation in science (B.tech in CSE / IT / EC or BCA ) you will need to start with Certified Python Programmer to have a good base of programming and where you can develop hacking tools using it. After completion of python programming certification, you will be eligible for this ethical hacking course and then complete it with Certified Web Application Penetration testing which focuses on actually exploiting vulnerabilities in web-based applications which is in huge demand all around the globe
If you had your graduation in arts, commerce or any other stream other than science you will need to start with Certified Network Professional Which follows the CCNA global course module to be eligible for this course and complete it with Certified Network Penetration Tester course which is a high-end specialization course. After completion of all the courses, you can apply for network penetration tester jobs.
Learn from Industry Experts & Get Real Hands-On Experience and get job ready

Get Started with FREE Demo Class:
* We don’t share your personal info with anyone. Check out our Privacy Policy for more info.
Why You Should Choose ICSS ?
Industry professions from Amazon, Cognizant & Intel will share their practical experience in the class
100% practical and lab-based classes (available online & offline)
25% Scholarship program for merited students with a minimum of 90% marks in their board exams
LIFETIME access to video tutorials, case studies
EMI option is available if you go for 2 or more courses.
Get educational loan @ O% interest
TRAINING METHODOLOGY of ICSS
With our full Training Methodology you will get job

JOB ORIENTED ETHICAL HACKING COURSE DETAILS
100% Job Placement Assistance
- Career Guide: Job Opportunities will be shared with you
- Be JOB Ready Resume prepared by Experts
- Questions & Answers provided for interviews
- Mock Exams you will write to test your skills
- Mock Interviews to boost your confidence
- Pre-Requisite: Any one can learn Ethical Hacking and Get Job
- Projects: You work on Real Life Case Studies
Course Duration
We Provide:
- 40 Hours Classes
- Fast Track Classes
- Weekdays & Weekend Classes
- In Class, You Get In-Depth ethical hacking Knowledge on each Topic
- Projects to do assignments
- Location: Courses are run in our Kolkata training center (Salt Lake, Sector 5) & Bangalore (Indiranagar)
- Corporate Training for your Employees
- Online Ethical Hacking Courses - Live Instructor LED Classes
- Pay only after attending FREE DEMO CLASS
C|EH v11 - Course Module
- What is Hacking
- What is Ethical Hacking
- Types of Hackers
- White Hat Hacker
- Black Hat Hackers
- Gray Hat Hackers
- Script Kiddies
- Hacktivists
- Spy Hackers
- Cyber Terrorists
- Vulnerability
- Exploit
- Remote Exploit
- Local Exploit
- Zero-day
- Zero-day vulnerability
- Zero-day Exploit
- Brute force attack
- Phishing
- Remote access
- Payload
- Active Information Gathering
- Passive Information Gathering
- Scanning
- Gaining Access
- Maintaining Access
- Covering Tracks
- Viruses
- Worms
- Trojan Horse
- Spyware
- Adware
- Backdoor
- Rootkits
- Ransomware
- What is Penetration Testing
- Types of Penetration Testing
- What is white box Penetration Testing
- What is Black Box Penetration testing
- Introduction to Linux OS
- Social Engineering
- Google Hacking Database
- Social Engineering the art of Human Hacking
- Gaining Target information using Google Dorks
- What is Virtual Machine
- What is VMware
- What is Virtual Box
- Install VMware
- Install Kali Linux
- Install Windows XP
- Install Windows 7
- Install Windows 10
- Install Add on in Mozilla
- Tamper Data
- Burp Suite
- No-Redirect
- Install Nessus
- System Hacking using Kon-Boot
- Network Scanning
- Port Scanning
- Service Scanning
- What is Nmap
- Scanning With Nmap
- Nmap Commands
- What is Metasploit?
- Xp Remote Exploit using Metasploit
- Msfvenom
- Windows 7 UAC Bypass
- SE-Toolkit Usages
- Create Phishing page with SE-Toolkit
- Hacking Facebook & Gmail password
- Types of Sniffing
- Network Sniffing with Wireshark
- Get FTP Login Details Using Wireshark
- What is RAT ?
- Exploit With RAT
- Protect System from RAT
- Details of DOS
- What is D-DOS
- D-DOS Attack
- Wireless Encryption
- Hacking WPA 2
- Wireless Spoofing Attack
- How Web Application Works
- Request and Response
- Installing Scanner (Acunetix, Netsparker)
- Scanning Website
The point of using dummy text for your paragraph is that it has a more-or-less normal distribution of letters. making it look like readable English.
- What is SQL-Injection ?
- Types of SQL-Injection
- Live Demo on SQL-Injection
- Types of XSS
- Live Demo on XSS All types
- What is CSRF?
- Live Demo On CSRF
- Create a Phishing Page
- What is Web Shell ?
- LIVE Demo on Web Server Hacking
- What is Broken Authentication?
- LIVE Demo on Broken Authentication
- What is Parameter Tampering?
- LIVE Demo on Parameter Tampering
- What is Session Hijacking?
- Android RAT Creation
- Android Hacking using Metasploit
- Android Hacking using Droidjack
- Android Hacking using L3mon
- Report Creation
- Penetration Testing on Vulnerable Assets
- Documentation
- Using Penetration Testing Tools
Class Room Training
Course Fee
INR 32,000 / - + 18% GST
Course Duration - 40 Hours
3 Months Training
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Online Self Paced LIVE Training
Course Fee
INR 32,000 / - + 18% GST
Course Duration - 40 Hours
3 Months Training
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Achievements of our Students
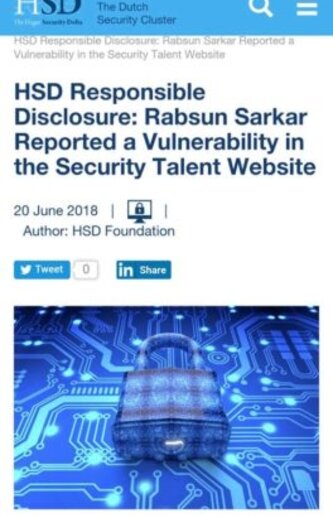
Many of our students have founded Zero-Day Vulnerabilities and also their CVE has published on Exploit-DB. Check their CVE and also read their Blog on Exploit DB.
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
RECENT PLACEMENTS
CEH Course in Chandigarh
CEH Course in Chandigarh by Indian Cyber Security Solutions is the most demanded CEH training in Chandigarh as well as in India. More than 1000+ student placed in different company after CEH Course in Chandigarh. This city attracts millions of IT professional to keep the IT dream alive. So it is great opportunity to all Chandigarh students. You are on the right track if you are thinking of doing a CEH Training in Chandigarh as some of the most promising Indian start-ups and the biggest companies of the world have offices in this city.
Today, companies across the world are struggling with the issue of data and network security. CEH Course in Chandigarh will prepare you for security professional to work as an Ethical Hacker and Penetration Tester. This course confirms the capacities of an ethical hacker to prepare for vulnerabilities of system foundation and prevent illegal hacking. The most ideal approach to do this is by understanding the strategies utilized by hackers to interfere into systems.
CEH from EC-Council is one of the most demanding course for IT security specialists, especially for those, who are looking for job prospects in penetration testing. In spite of the fact that the certification is must be required for entrance analyzers and its focal points are not limited.
This Course acts as the foundation stone in your career to be a Penetration Tester and providing security to networks and websites. Hacking is a technique by which a person can bypass system’s defence. Ethical Hackers use the same technique instead of taking advantage of any vulnerabilities that are found they document them and provide actionable advice on how to fix them. The purpose of ethical hacking is to evaluate the security of and identify vulnerabilities in systems, networks or system infrastructure.
Need to Work on real-time projects and complete assignments to get Professional Certification from Indian Cyber Security Solutions
ICSS provides the course completion certificate once you successfully complete the Certified Ethical Hacking training program Professional Certificate Holders work at 1000s of companies like HP, TCS, Amazon, Accenture and many more.
REGISTRATION DESK
Current Job Openings
Check job profile, salary scale of current jobs available in market
CEH Certification Course in Chandigarh
is what students & working professionals are looking for career opportunity in the cyber security field
CEH Certification Course in Chandigarh offers 100% placement assistance to our students for a corporate career. Today’s digital era, one of the biggest threats comes from cybercriminals. Hackers were not taken seriously until a few years back. In addition, some big names in the Indian industry had to pay a large amount of money to hackers. So that they keep the information confidential. According to surveys guided by cyber security firms in the country, Indian firms lost more than $4 billion in 2013 alone because of hackers. Our trainers are not just trainers, they are Industry Experts. You will get hands-on training during CEH Certification Course in Chandigarh. CEH training in Chandigarh is a highly-valued certification. You will be able to get the desired job in this field. Ethical hackers work as information security professionals and are considered notable in all information technology zones. Certified Ethical Hackers keep a check on security issues related to Information Security. Ethical Hackers are hired by all organizations those who have critical business data online.
What does an organization expect from a Cyber Security Professional?
Our training module is delicately balanced between practical lab based training and theoretical content. Organizations expect real time practical based solutions to the real world threat of cyber attack. Focusing on practical training conducted by Bug Bounty hunters and exploit writers. ICSS CEH Certification Course in Chandigarh will surely give you the edge and help you to grab the job. Our CEH v11 program also focuses on the most important aspect of “Documentation” / “VAPT Reporting”.
Cyber security professionals will not only impart you with latest cyber security training but will also help you to prepare and report critical vulnerabilities to companies as a bug bounty hunter and also helps you in VAPT report writing. For an organization a cyber security professional who has technical and as well as reporting / documentation skill will always be the first choice.
This reduces the investment of organizations on the newly recruited cyber security professional. There is a huge demand for ethical hackers and the CEH Certification Course in Chandigarh. So you can take help to brighten your job prospects in some of the biggest global companies in the world.
The CEH Training in Chandigarh is a new credential in the IT certification industry, but its importance and influence have grown quickly. Indian Cyber Security Solutions is proud to be the highest rated CEH certification training institute in Chandigarh with around 1890+ students taking admission every year across the globe. CEH Certification Course in Chandigarh is highly demanded as all companies whether big or small require cybersecurity professionals to prevent data breaches. Individual students who opt for CEH Certification Course in Chandigarh could expect a minimum of 3.0 Lakh package salary as fresher’s around the globe.
Collages where we have conducted Cyber Security & Ethical Hacking training session
Some Glimpses of our Workshop
Best CEH Training Institute in Chandigarh,Punjab
Best CEH Training Institute in Chandigarh,Punjab Indian Cyber Security Solutions will give you vast knowledge about hacking. Ethical hackers use their skills and many of the same methods and techniques to test and bypass organizations’ IT security as their unethical counterparts, who are referred to as black hat hackers. The trainers are industry professionals. They work in many projects. Becoming Ethical hackers you can find security exposures in insecure system configurations, known and unknown hardware or software vulnerabilities as well as operational weaknesses in process or technical countermeasures.
Ethical hackers help companies determine which of their IT security measures are effective, which need to be updated and which contain vulnerabilities that can be exploited. When ethical hackers finish evaluating organizations’ systems, they report back to company leaders about those vulnerable areas, for instance, a lack of sufficient password encryption, insecure applications or exposed systems running un-patched software. Cyber attacks can cripple or destroy a business, especially a small business. However, most companies are completely unprepared for cyberattacks.
Ethical hackers understand how threat actors operate and they know how these bad actors will use new information and techniques to attack systems. You will learn all these things from ICSS, Best CEH Training Institute in Chandigarh,Punjab. After CEH Training in Chandigarh you can the hacking skills to protect any organizations’ website. However if you want to join an institute for learning Ethical hacking then you can join ICSS, Best CEH Training Institute in Chandigarh,Punjab. Ethical hackers generally use the same hacking skills that malicious actors use to attack enterprises. Ethical Hacking has been a lucrative career option for many, and not without good reason! It’s a challenging job that never gets boring, pays well and also brings a greater sense of achievement.
Indian Cyber Security Solutions conducts campus placement drive for students within few months after completion of the cyber security course. ICSS conducts soft skills classes for students to enhance their soft skills which are highly required to crack interviews. Check out our placement records where we have displayed emails and letters which have come to us for conducting job interviews. MNC’s like PWC , ITC and CTS had recruited ICSS students since 2018. We sincerely believe that after the intense practical lab based training on cyber security conducted by ICSS you as an individual will definitely be self sufficient to crack any job which requires cyber security skills. CEH v11 course module is designed as per the industry demand which is evident from the job postings made by recruiting companies in different job portals.
Still Hunting for a Job? or Want to Make a Career Switch into CEH?
Recruiters are looking for you!
All you need to Learn Basic to Advance of CEH with ICSS, Become Certified Professional and Get JOB with our Free Placement Assistance Program
Cyber Security Course in Chandigarh and workshops conducted by ICSS Educational Division
Cyber security course in Chandigarh and workshops are conducted across all collages. ICSS had been fortunate enough to have been associated with some of the renounced educational institutions like IIT Kharagpur, NIT Durgapur, Jadavpur University, Lovely Professional University and JIS collage to name a few. Our campus representatives are highly active and conduct interactive sessions on cyber security. Campus representatives are student’s representatives from different collages those who are responsible for establishing a research lab on cyber security inside the campus of the respective collages. These research facilities & interactive sessions on ethical hacking helps the students to gain latest knowledge in cyber security. Indian Cyber Security Solutions offers Cyber security course in Chandigarh for corporate teams and individuals.
Do you want to be a Campus Representative?
If you want to be a CR there is a long list of benefits that you will be entitled too