OSCP training in Hyderabad
with Placement by Indian Cyber Security Solutions
OSCP training in Hyderabad by ICSS offers a comprehensive curriculum for aspiring cybersecurity professionals. Our program covers essential topics like network security, penetration testing, and vulnerability assessment. By enrolling, you gain hands-on experience through practical labs and real-world scenarios. This training equips you with the skills needed to protect organizations from cyber threats. Whether you're a beginner or an experienced IT professional, our expert instructors will guide you through every step. Join our OSCP training in Hyderabad to enhance your career prospects in the rapidly growing field of cybersecurity.
The OSCP training in Hyderabad by Indian Cyber Security Solutions, jointly certified by the Hyderabad Institute of Cyber Security, is ideal for those looking to build a successful career in cybersecurity. Our course provides in-depth knowledge of hacking tools and techniques, ensuring you stay ahead of cybercriminals. Participants will learn to identify and mitigate potential security threats, making them invaluable assets to any organization. With a strong focus on practical learning, our OSCP training in Hyderabad ensures you master the skills needed to secure digital infrastructures. Enroll today to start your journey towards becoming a certified OSCP trainers and safeguard the digital world.
OSCP training in Hyderabad, designed by experienced penetration testers with over 15 years of experience, is your gateway to a rewarding job in cybersecurity. This comprehensive training signifies deep understanding and commitment, making you stand out to employers. Indian Cyber Security Solutions offers a robust framework, equipping you for roles like penetration tester or cybersecurity expert.











With attractive packages and promising career growth, our graduates are making significant strides in the industry. The images of our placed students, along with their impressive packages, highlight the real-world impact of our comprehensive training program.
Our recent placement records speak volumes about the success of our OSCP training in Hyderabad. At Indian Cyber Security Solutions (ICSS), we pride ourselves on providing top-notch education that prepares students for the demanding cybersecurity job market. Our students have secured prestigious positions in leading MNCs such as Wipro, TCS, Amazon, and many more.






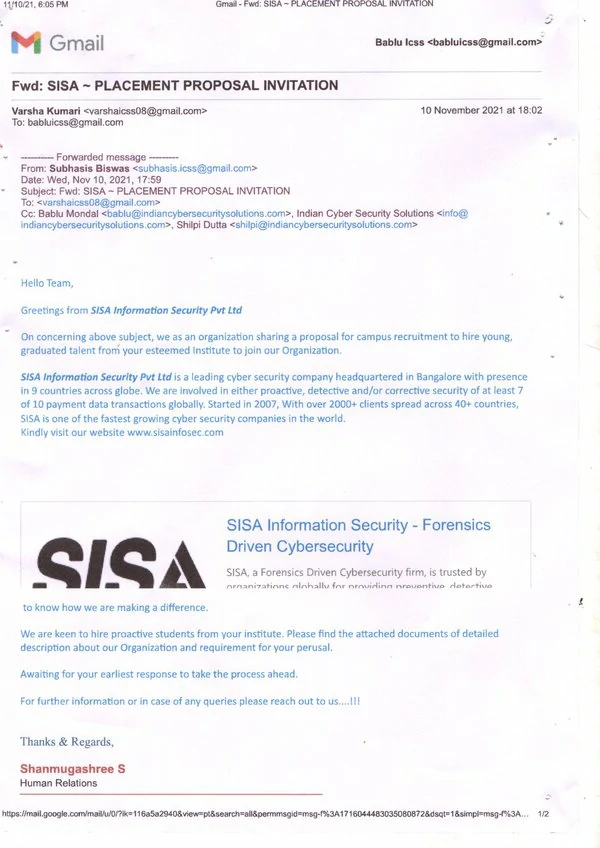
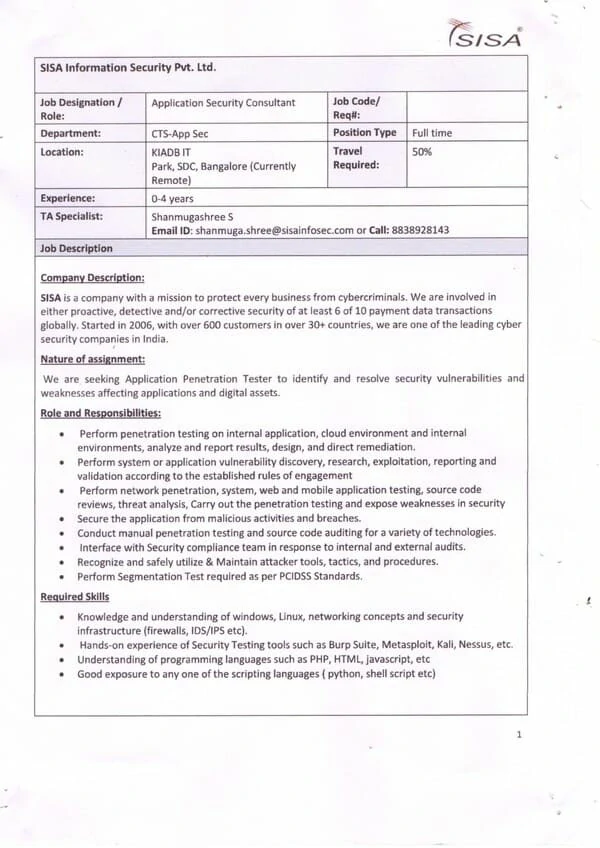




Join our OSCP training in Hyderabad and take advantage of our strong industry connections and proven placement track record. Secure your future with ICSS and become a part of the elite group of cybersecurity professionals who are shaping the future of digital security.
OSCP Training Course in Hyderabad by ICSS is the Highest-Rated Cyber Security Course
OSCP Training Course in Hyderabad conducted by Indian Cyber Security Solutions ensures you receive top-notch education from industry experts. Our cyber security trainers are seasoned professionals with extensive experience in cybersecurity working as full-time penetration testers with us & are involved in VAPT projects conducted by ICSS. They bring real-world knowledge into the classroom, providing you with insights that go beyond textbooks.
The OSCP Training course in Hyderabad also includes up-to-date content that covers the latest trends and threats in the cybersecurity landscape. By choosing our OSCP training in Hyderabad, you get the opportunity to network with like-minded peers and industry professionals, creating valuable connections that can help advance your career.
If you are opting for the OSCP Training course in Hyderabad by ICSS which opens up numerous career opportunities in the field of cybersecurity.
The OSCP Training in Hyderabad offered by Indian Cyber Security Solutions is a comprehensive program designed to equip individuals with the necessary knowledge and skills to excel in the field of penetration testing and offensive security. With a focus on hands-on training and an industry-relevant curriculum, this course is ideal for both beginners and experienced professionals seeking to enhance their expertise in penetration testing.The course covers a wide range of topics, starting from the fundamentals of penetration testing to advanced concepts such as network exploitation, buffer overflow attacks, privilege escalation, and post-exploitation techniques. The curriculum is carefully designed to provide a step-by-step learning approach, ensuring that students grasp each concept thoroughly before progressing to more advanced topics.One of the key advantages of the OSCP Training in Hyderabad is the expertise of the faculty. The instructors at Indian Cyber Security Solutions are experienced professionals with extensive knowledge and practical experience in penetration testing and offensive security. They bring their real-world experience into the classroom, offering valuable insights and practical examples to enhance the learning experience.If you are looking for OSCP Training in Hyderabad, ICSS should be your top choice for industry-leading training in offensive security.
The course also emphasizes hands-on training and practical exercises, allowing students to apply their knowledge in real-world scenarios. The institute provides well-equipped computer labs with the latest tools and software necessary for cybersecurity training. This enables students to gain practical experience in using industry-standard cybersecurity tools and techniques. By enrolling in the OSCP training in Hyderabad, students not only gain theoretical knowledge but also have the opportunity to work on real-world projects and case studies. This practical exposure helps them develop problem-solving skills and enhances their understanding of the concepts learned in the classroom. It also prepares them to tackle real-world cybersecurity challenges effectively. One of the key advantages of the OSCP Training Course in Hyderabad is the expertise of the faculty. The instructors at Indian Cyber Security Solutions are experienced professionals with in-depth knowledge and practical experience in the field of cybersecurity. They bring their industry experience into the classroom, providing real-world insights and practical examples to enhance the learning experience.
Indian Cyber Security Solutions offers a OSCP Training Certification in Hyderabad, providing an exceptional opportunity for those seeking a career in cybersecurity. This program prepares you for the growing demand in the field, offering industry-recognized certification upon completion. With assistance in job placement and partnerships with top cybersecurity firms, the certification opens doors to a wide range of global employment opportunities. Gain practical experience and industry recognition, making it a wise investment in your professional future in the digital world.
Indian Cyber Security Solutions & Hyderabad Institute of Cyber Security

OSCP Training Institute in Hyderabad
with a state-of-the-art facility for aspiring cyber security students
OSCP Training Institute in Hyderabad which offers a robust curriculum designed to meet the needs of aspiring cybersecurity professionals is what all aspiring cybersecurity students are looking for. Our institute provides comprehensive training that covers essential topics such as network security, penetration testing, and vulnerability assessment. OSCP training in Hyderabad conducted jointly by the Indian Institute of Cyber Security & Indian Cyber Security Solutions ensures that you gain hands-on experience through practical labs and real-world scenarios.
By choosing our institute, you benefit from the expertise of seasoned trainers and the opportunity to network with industry professionals. This makes our OSCP Training Institute in Hyderabad the ideal choice for your cybersecurity education.
Indian Cyber Security Solutions provides numerous advantages for those pursuing a career in cybersecurity. Our courses are regularly updated to reflect the latest trends and threats in the cybersecurity landscape. OSCP training in Hyderabad at our institute guarantees that you stay ahead of the curve with cutting-edge knowledge and skills. Our alumni have successfully secured roles as penetration testers, security analysts, and network security engineers. By enrolling in our OSCP Training Institute in Hyderabad, you can enhance your career prospects and become a valuable asset to any organization in the digital age.


OSCP Training Certification in Hyderabad by the Indian Institute of Cyber Security is among the most demanded & recognized certification in the Industry
OSCP Training Certification in Hyderabad by the Indian Institute of Cyber Security offers a valuable credential for professionals aiming to excel in the cybersecurity field. If you are opting for the OSCP training in Hyderabad from us, rest assured that it provides a rigorous certification program that ensures participants acquire practical skills and comprehensive knowledge. OSCP training in Hyderabad conducted jointly by the Indian Institute of Cyber Security & Indian Cyber Security Solutions includes real-world scenarios and hands-on labs to prepare you for the challenges faced by cybersecurity experts.
Earning this certification not only enhances your resume but also demonstrates your commitment to protecting digital infrastructures. With OSCP Training Certification in Hyderabad, you can confidently pursue advanced career opportunities and make a significant impact in the cybersecurity domain.
Opting for the OSCP Training certification in Hyderabad opens doors to a wide range of career opportunities in the ever-growing field of cybersecurity. Our training department equips you with the expertise needed to tackle complex security issues and mitigate potential threats. Our cyber security course in Hyderabad includes up-to-date content on the latest cybersecurity trends, ensuring you remain knowledgeable and proficient.
This certification validates your skills and makes you a desirable candidate for positions such as penetration tester, security analyst, and network security engineer. By obtaining OSCP Training Certification in Hyderabad, you demonstrate your dedication to maintaining robust security measures in the digital age.
At Indian Cyber Security Solutions (ICSS), we strategically offer our OSCP training in Hyderabad, conveniently located at College More. This prime location makes it easier for our students to secure placements with leading companies in the area. For those coming from far-off places, our proximity to popular student areas like Kestopur and New Town—just 10 minutes away—provides ample accommodation options to suit every preference. Being situated in Hyderabad’s tech hub, students benefit from a dynamic environment that enhances their learning and job opportunities. Our OSCP training in Hyderabad ensures that you have the credentials and expertise needed to stand out in the job market, making you an essential asset in the digital age. Enroll now to take advantage of our premium training and exceptional placement opportunities in Hyderabad.
Since 2016, Indian Cyber Security Solutions (ICSS) has become the leading OSCP Training Institute in Hyderabad. Our program is designed to equip students with the skills needed to excel in the cybersecurity field. With a strong emphasis on practical, hands-on training, our graduates are well-prepared for the challenges of the industry.
ICSS boasts a stellar placement record, with students securing positions in prestigious companies like Wipro, TCS, and Amazon. Located in Sector V, Hyderabad's IT hub, we provide students with excellent opportunities for networking and on-campus recruitment.
Our success over the years is a testament to our commitment to quality education and student success. Join ICSS and become part of a legacy of excellence in cybersecurity training. Enroll in our OSCP Training Institute in Hyderabad today and take the first step towards a promising career. Visit our website to learn more and register now!