Indian Cyber Security Solutions
in association with
Indian Institute of Cyber Security


Ethical Hacking Training in Bangalore - EHP (Ethical Hacking Professional) Course
Ethical Hacking Training in Bangalore by Indian Cyber Security Solutions is the most demanded training in the globe. We are living in the modern era and our daily life based on technology. Nowadays the internet is a common name known to us. As internet usage is increasing day by day so our world is becoming small and people coming closer to one another. Indian Cyber Security Solutions is the Best Ethical Hacking training institute in Bangalore because we provide 100% practical-based Ethical Hacking Course in Bangalore.
Given the growing need for qualified individuals, ethical hacking training in Bangalore gives you a rare opportunity to succeed in the cybersecurity industry. Bangalore, sometimes referred to as the "Silicon Valley of India," is well-known for its growing IT sector and technical achievements. Bangalore, the nation's top IT center, is home to a sizable Wi-Fi infrastructure network and has been essential to India's technical, historical, educational development. Bangalore is currently the fourth-largest city in India and a significant commercial center in the south of the nation. The city's diversified businesses, which include petrochemicals, financial services, software services, and automotive manufacturing, are responsible for its economic success. Engaging in Ethical Hacking Training in Bangalore might open up a lot of opportunities for you. If you are looking to kick start your career in cyber security, trust Indian Cyber Security Solutions to provide you with the knowledge, skills, and real-world opportunities to thrive. Join us today and unlock your potential in the dynamic field of cyber security.
Enroll for
Online Live Class
Get Started with FREE Demo Class
Our Ethical Hacking Training in Bangalore goes in-depth into the techniques used by Black Hat hackers. As these hacking skills can be used in a bad way, our ethical hacking course will teach you how you can use the same skills to protect the intellectual property of organizations and individuals and become a white hat hacker. The Ethical Hacking Professional (EHP) certification training program aims at providing the highest level of the technical skillset required to get into the field of cybersecurity. The ethical hacking course in Bangalore goes in-depth into the techniques used by Black Hat hackers and demonstrates it live in a lab-based 100% practically oriented class.
Ethical Hacking training in Bangalore provides Ethical Hacking Professional certification or EHP which enables us to analyze as well as understand computer security procedures through which corporate firms can be protected from any malicious data breaches. Indian Cyber Security Solutions Ethical Hacking Course in Bangalore you get the certification that examines how much a student can use tools of penetration system so as to test systems in computer and security network and implement the same for ethical hacking.
Get First 2 Classes for FREE
(NO Advance Payment Required)
Congratulations to Shibashish Saha, a talented student of Indian Cyber Security Solutions, for securing an internship with a stipend of 20,000 INR per month!
We are thrilled to see Shibashish's hard work and dedication paying off, and we are proud to have played a part in his success.At Indian Cyber Security Solutions, we prioritize the growth and professional development of our students. We believe in providing them with real-world opportunities to apply their skills and knowledge. We do not engage in fake placements or internships. The screen shots displayed are proof of Shibashish's accomplishment and our commitment to genuine career opportunities. Shibashish's achievement is a testament to the quality of our training programs and the expertise of our instructors.
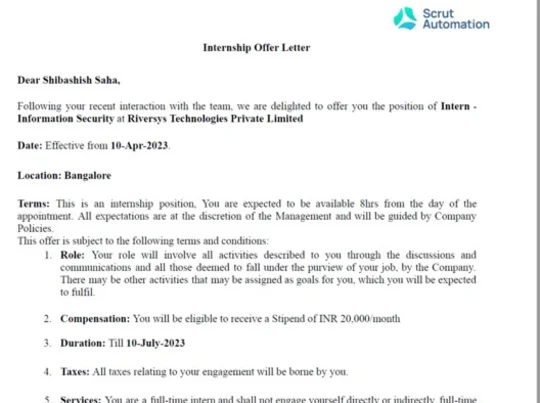

We strive to equip our students with the practical skills and industry insights needed to excel in the field of cyber security and ethical hacking training in Kolkata. We congratulate Shibashish once again on his well-deserved internship and wish him all the best in this new chapter of his professional journey. We are confident that he will make a significant impact and gain valuable experience during his internship. At Indian Cyber Security Solutions, we remain committed to providing our students with the best education, genuine placement opportunities, and a solid foundation for a successful career in cyber security. We take pride in our students' achievements and look forward to witnessing many more success stories in the future.

Indian Cyber Security Solutions is awarded the 2nd position as the
" 10 Most Promising Cyber Security Training Institute in India 2020 "
Ethical Hacking Training in Bangalore by Indian Cyber Security Solutions is the most demanded training in the globe. We are living in the modern era and our daily life based on technology. Nowadays the internet is a common name known to us. As internet usage is increasing day by day so our world is becoming small and people coming closer to one another.
Ethical Hacking training goes in-depth into the techniques used by Black Hat hackers. As these hacking skills can be used in a bad way, our ethical hacking course will teach you how you can use the same skills to protect the intellectual property of organizations and individuals and become a white hat hacker. The Ethical Hacking Professional (EHP) certification training program aims at providing the highest level of the technical skillset required to get into the field of cybersecurity.
The Ethical Hacking Course in Bangalore goes in-depth into the techniques used by Black Hat hackers and demonstrates it live in a lab-based 100% practically oriented class.
Our Achievement

FAQs
Ethical Hacking Course in Bangalore by one of the best ethical hacking training institute in Bangalore, Indian Cyber Security Solutions is INR 15000 only (Ethical Hacking Professional – EHP). This ethical hacking training course is available both online and in classroom training mode.
The salary of an ethical hacker in Bangalore can vary depending on factors like experience, certifications and the organization they are working for. But it is important to note that following ethical hacking training in Bangalore can significantly increase your earnings in this field. With growing concerns about cybersecurity, ethical hackers are in high demand. Organizations across industries are increasingly investing in cyber security measures to protect their valuable data and systems. This has led to an increase in the demand for skilled people who can anticipate vulnerabilities and secure systems.
With proper hacking ethics training in Bangalore, employees can expect competitive salaries. Entry level ethical hackers in Bangalore can earn a salary of 4 to 6 lakhs per year. As they gain experience and expertise, this number can rise exponentially, with middle-class earning around Rs 8 to 12 lakh a year Sea ethical senior hackers with a few years of experience and additional credentials can command a salary increasing, in the range of Rs 15 to 30 million or more per annum Additionally, ethical hackers who constantly update their skills and keep up to date with the latest trends and techniques through ethical hacking training in Bangalore can gain career advantage as Ethical Hacker, Certified Information Systems Security Professional (CISSP), or Certifications such as Offensive Security Certified Professional (OSCP) can also contribute to higher salaries Notably, salary levels can vary depending on the organization, the job, and the individual discussion. But ethical hacking training in Bangalore gives you the knowledge and skills necessary to excel in this field and increase your chances of earning competitive salaries in the growing cybersecurity sector is a great deal.
It can take anywhere from a few months to a few years to become an ethical hacker, depending on your level of experience and expertise. For those just starting out, you can enroll for EHP course by Indian Cyber Security Solutions which will only take 3 months. ICSS even offers 100% placement assistance.
Hacker course fees can vary depending on the training provider and the specific course you choose. However, at Indian Cyber Security Solutions, the leading organization offering ethical hacking courses in Bangalore, the cost of the courses is expensive and very competitive and our comprehensive ethical hacking courses are available Only INR 15,000. At Indian Cyber Security Solutions, we understand the importance of making proper cyber security training available to prospective employees. Our ethical hacking course in Bangalore is designed to give you the in-depth knowledge and practical skills required to excel in terms of ethical hacking. As well as providing high-quality training for experienced industry professionals, we strive to keep our course fees reasonable and highly accessible to enthusiastic students. By enrolling in our ethical hacking course, you can gain knowledge in various hacking techniques, techniques and tools used by cybersecurity professionals. Our experienced, professional cybersecurity instructors will guide you through hands-on exercises, real-life case studies and infrastructure projects. Additionally, our course includes regular assessments, personalized attention, and further construction assistance to help launch your career in ethical hacking. Don’t miss out on this amazing opportunity to hone your skills and start a successful career in the cyber security industry. Join our Ethical Hacking Course in Bangalore at Indian Cyber Security Solutions for an in-depth learning experience at an affordable cost of 15,000 INR. Take the first steps to becoming an ethical hacking expert and secure your future today!
The average salary for a Ethical Hacker is ₹5,21,271 per year in Bangalore. Indian Cyber Security Solutions have mentored students who got placed at a higher package because of their industry best trainers with 10+ of experience.
EHP provided by Indian Cyber Security Solutions is a 3 months certification course where anyone with a Bachelor's degree (BSc, BTech, BE, BCA, even BA or BCom students) to become an ethical hacker. Candidates having an advanced diploma in network security can also opt for ethical hacking as a career. Even after 12th they can go for Diploma in Cyber Security provided by ICSS.
Ethical Hacking Professional by Indian Cyber Security Solutions is the best certificate course for ethical hacking due to their experienced trainers and low cost. ICSS have trained over 5000 students over the years and 500+ students have been placed in the industry.
EHP – Ethical Hacking Professional
Bangalore is known as the IT Capital of India. There is great hope to hire cybersecurity in companies. By Ethical Hacking training in Bangalore, you will develop the ability to measure and mitigate threats and find out where your organization is more vulnerable to be hacked.
One can work as an Information Security Expert, Security Administrator, Security Analyst, Ethical Hacking Trainer, or Penetration Tester after successfully carrying out the Ethical Hacking Course in Bangalore.
Ethical Hacking training in Bangalore with hands-on training in the lab from the professional hackers who are themselves Ethical Hacking Professional, OSCP Certified. Cyber Security training is in huge demand as organizations are going online with more than 170 Billion Dollar investment in the cyber security domain worldwide.
At Indian Cyber Security Solutions, you will learn in-depth on an attacker can hack an organization and also how the defend the intellectual property of the organization from being hacked. Ethical hacking training is designed is such a way that you get the maximum practical knowledge. At our training center, we bring in guest faculties from the industry so they can share their practical experience with you. At the end of the course, we aim to make your placement ready.
Indian Cyber Security Solutions have 130+ trainers who are professional Ethical Hackers working in different MNCs like Infosys, Cognizant, Wipro, ATOS, Intel and are also members of our research & development team. All the trainers are geographically located in different areas provide online training on Ethical Hacking.
All the ethical hacking training classes are held through an application where the faculty and the students are LIVE interacting with each other over the internet. All the classes are recorded and uploaded in our online portal “ HACKERS LAB “ where all students have lifetime access. We guarantee your satisfaction or we pay back your course fee. There will be 3 instructors dedicated to individual batch which will carry on for 3 months.
Eligibility Criteria to become a Professional Ethical Hacker
The prime objective of this course is to make you ready for the industry where you can use your skills to protect the organization. After completion of this course, you will be able to successfully document the Vulnerability Assessment report for the organization.
Tools that will be covered by Indian Cyber Security Solutions:
Upcoming Batches
01-10-2023 | Weekdays | Thursday (Monday - Thursday) | ||
03-10-2023 | Weekend | Saturday (Saturday - Sunday) | ||
05-10-2023 | Weekdays | Monday (Monday - Friday) | ||
10-10-2023 | Weekend | Saturday (Saturday - Sunday) |
Trainers Profile
- Indian Cyber Security Solutions (ICSS) trainers emphasize blended learning.
- Trainers at ICSS utilize real-life projects and case studies to provide practical knowledge of Ethical Hacking and Hackers.
- ICSS Ethical Hacking trainers in Bangalore have 12+ years of experience in the Networking field.
- Trainers at ICSS are working professionals from the cybersecurity field.
- ICSS trainers provide corporate training to enrich students' knowledge and industry-relevant skills.
- Regular assessments and individual attention are given to students for their progress.
- ICSS Ethical Hacking trainers assist students in resume building and develop their interpersonal skills.
Why You Should Choose ICSS ?
Industry professions from Amazon, Cognizant & Intel will share their practical experience in the class
100% practical and lab-based classes (available online & offline)
25% Scholarship program for merited students with a minimum of 90% marks in their board exams
LIFETIME access to video tutorials, case studies
EMI option is available if you go for 2 or more courses.
Get educational loan @ O% interest
Learn from Industry Experts & Get Real Hands-On Experience and get job ready

Get Started with FREE Demo Class:
* We don’t share your personal info with anyone. Check out our Privacy Policy for more info.
RECENT PLACEMENT RECORDS
Achievements of our Students
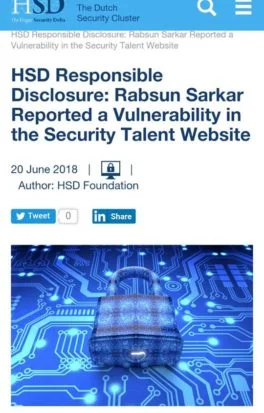
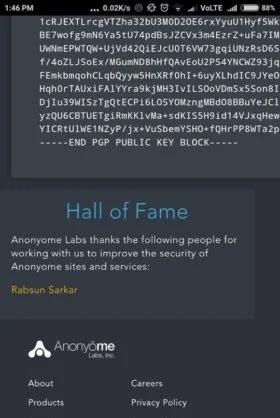
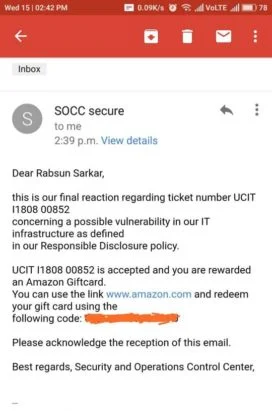
Many of our students have founded Zero-Day Vulnerabilities and also their CVE has published on Exploit-DB. Check their CVE and also read their Blog on Exploit DB.
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
Ethical Hacking Professional - Course Module
Module 1: Introduction To Ethical Hacking
Module 2: Information Gathering Techniques
Module 3: Introduction to Basic Networking
Module 4: Network Scanning and Enumeration
Module 5: Host and Device Vulnerability Assessment
Module 6: Vulnerability Analysis
Module 7: Malware Analysis and Defense
Module 8: System Hacking
Module 9: Network Packet Analysis and Sniffing
Module 10: Social Engineering and Human Manipulation Attack
Module 11: Denial-of-Service (DoS)
Module 12: Bypassing Firewalls and Honeypots
Module 13: Hacking Web Servers
Module 14: Web Fundamentals
Module 15: Web Application Security
Module 16: SQL Injection and Injection Attacks
Module 17: Wireless Network Security
Module 18: Android Hacking
Module 19: IOT Penetration Testing
Module 20: Introduction to Cloud Computing
Module 21: Cryptography and Data Protection
Class Room Training
3 Months Training
Course Fees: INR: 15,000/- + 18% GST
2 Classes Per Week X 2 Hours Each Day
Week End Classes | Week Days Classes
Online Self Paced LIVE Training
3 Months Training
Course Fees: INR: 15,000/- + 18% GST
2 Classes Per Week X 2 Hours Each Day
Week End Classes | Week Days Classes
Still Hunting for a Job? or Want to Make a Career Switch into Cyber Security ?
Recruiters are looking for you!
All you need to Learn Basic to Advance of Ethical Hacking from ICSS, Become Certified Professional and Get JOB with our Free Placement Assistance Program
Benefits of completing Ethical Hacking Training in Bangalore by Indian Cyber Security Solutions
The EHP course by ICSS provides hands-on training in ethical hacking and information security, making you job-ready. It covers the latest tools, techniques, and techniques in the industry. With a certification from ICSS, you can confidently apply for ethical hacking and information security roles in MNCs.
CITI Group: CITI Group is recruiting Information Security Professionals, and to meet the eligibility requirements, EHP certification is required. ICSS offers EHP certification courses that can help professionals prepare for this role. It covers all important aspects of cybersecurity, from threats to countermeasures, and ensures candidates are fully equipped to address information security challenges. The average CTC as per Glassdoor is INR 11.50 LPA.
Deutsche Bank: Deutsche Bank Hires Information Security Professional professionals. The ICSS Ethical Hacking Professional (EHP) course can help candidates develop the skills necessary to apply for this position. The course provides hands-on training to identify vulnerabilities and protect against cyber threats, qualifying candidates for careers in information security. The average CTC as per Glassdoor is between INR 11-11.70 LPA.
ORACLE: Oracle is hiring computer forensics engineers, Network Security Engineers to enhance its cybersecurity capabilities. The ICSS-provided EHP course can help individuals develop the skills necessary to qualify for this role and excel in electronic forensic investigations. The average CTC as per Glassdoor is between INR 8-26 LPA.
Intel: Intel is hiring computer forensics engineers to help identify, investigate, and prevent cyber threats. ICSS’s EHP course can help individuals gain the necessary skills and complete advanced CHFI courses to secure such roles by providing them with knowledge in cyber forensics, incident response, and malware analysis.
Deloitte: Deloitte is hiring ethical hackers with salary up to INR 10-12 LPA. The ICSS EHP course can help candidates improve their skills in ethical hacking and cybersecurity, increasing their chances of getting a job with Deloitte. Enroll in the ICSS EHP course today and start your career in cyber security.
Accenture: Accenture is hiring ethical hackers with an average salary of ₹9,00,000 per annum. The ICSS EHP course can help individuals gain the necessary skills to become ethical hackers and get a job with companies like Accenture. Join ICSS and take your first step toward a successful career in cybersecurity.
IBM: IBM hires Network Security Engineers with an average salary of INR 7-9.75 LPA. The ICSS EHP course can help individuals develop the skills necessary to secure computer networks and prevent unauthorized access. Join ICSS and start your career in Network Security Engineering at IBM.
CISCO: Cisco Systems is hiring Network Security Engineers with salaries ranging from INR 7-10 LPA. Indian Cyber Security Solutions’ EHP course provides hands-on training and certification in network security, equipping candidates with the knowledge and skills required for a career in this field.
Ethical Hacking Course in Bangalore : Master Cybersecurity Skills
Ethical Hacking Course in Bangalore by Indian Cyber Security Solutions will teach you how to use the tools and techniques used by cybercriminals to perform a white-hat, ethical hack on your organization. Indian Cyber Security Solutions is rated one of the top training and giving best course in Ethical Hacking. Ethical Hacking training in Bangalore from Indian Cyber Security Solutions is the most demanded training in India. The Ethical hacking training in Bangalore course goes in-depth into the techniques used by Black Hat hackers and demonstrates it live in a lab-based 100% practically oriented class.
Today, companies across the world are struggling with the issue of data and network security. In fact, as per the 2018 Cost of Data Breach Study sponsored by IBM, the global average cost of data breach comes around $3.62 million.
As these hacking skills can be used in a bad way, our Ethical hacking course in Bangalore will teach you how you can use the same skills to protect the intellectual property of organizations and individuals and become a white hat hacker. During the course of ethical hacking, you will develop the ability to measure and mitigate threats and find out where your organization is more vulnerable to be hacked. Most of our students found Zero-day vulnerabilities. If you are looking to build a career in the field of cybersecurity you can enroll in our Ethical hacking course in Bangalore.
This Ethical hacking course in Bangalore verifies the skills required to thrive in the information security domain. Many IT departments have made Ethical Hacking compulsory for security-related posts. Ethical hacking professionals earn 44-percent higher salaries than non-certified professionals.
Need to Work on real-time projects and complete assignments to get Professional Certification from Indian Cyber Security Solutions
ICSS provides the course completion certificate once you successfully complete the Ethical Hacking training program Professional Certificate Holders work at 1000s of companies like HP, TCS, Amazon, Accenture and many more.
REGISTRATION DESK
Current Job Openings
Check job profile, salary scale of current jobs available in market
Cyber Security Professional | Cyber Security Engineer | Pen-Tester
Information Security Analyst | Security Consultant
Threat Hunter| Cyber Security Engineer | Pen-Tester
Network Engineer | Cyber Security Engineer | Pen-Tester
Best Ethical Hacking Training institute in Bangalore
Best Ethical hacking training institute in Bangalore where ICSS provides the hands on training with live projects. Since 2016 Indian Cyber Security Solutions had conducted 400+ cyber security workshop and training programs on ethical hacking in different collages across India. ICSS is rated among the best ethical hacking training institute in Bangalore providing the most advanced level hands on training program prepared by IT security professionals. As the demand for trained cyber security professionals had increased is recent past, students and working professionals are actively looking for practical based ethical hacking training in Bangalore.
What does an organization expect from a Cyber Security Professional?
Our training module is delicately balanced between practical lab based training and theoretical content. Organizations expect real time practical based solutions to the real world threat of cyber attack. Focusing on practical training conducted by Bug Bounty hunters and exploit writers. As the best ethical hacking training institute in Bangalore, ICSS will surely give you the edge and help you to grab the job. Our ethical hacking training program also focuses on the most important aspect of “Documentation” / “VAPT Reporting”. Cyber security professionals will not only impart you with latest cyber security training but will also help you to prepare and report critical vulnerabilities to companies as a bug bounty hunter and also helps you in VAPT report writing. For an organization a cyber security professional who has technical and as well as reporting / documentation skill will always be the first choice. This reduces the investment of organizations on the newly recruited cyber security professional.
Cyber Security Course in Bangalore, Karnataka Conducted by Indian Cyber Security Solutions
Cyber Security Course in Bangalore, Karnataka conducted by ICSS has seen huge rise in demand. Thanks to all our students who had been benefited from our EHP course. If you want to brush up on your penetration testing and network security analysis skills so you should join Cyber security course in Bangalore, Karnataka taught by industry experts, bug bounty hunters & exploit writers.
After successfully completing the cyber security course in Bangalore, Karnataka conducted by ICSS, students were able to crack cyber security job interviews. With 280+ students who had secured a job in the cyber security industry within few months after completion of the ethical hacking training in Bangalore itself.
How ICSS can help you to secure a Job ?
Indian Cyber Security Solutions conducts campus placement drive for students within few months after completion of the cyber security course. ICSS conducts soft skills classes for students to enhance their soft skills which are highly required to crack interviews. Check out our placement records where we have displayed emails and letters which have come to us for conducting job interviews. MNC’s like PWC , ITC and CTS had recruited ICSS students since 2018. We sincerely believe that after the intense practical lab based training on cyber security conducted by ICSS you as an individual will definitely be self sufficient to crack any job which requires cyber security skills. EHP course module is designed as per the industry demand which is evident from the job postings made by recruiting companies in different job portals.
Cyber Security Course in Bangalore and workshops conducted by ICSS Educational Division
Cyber security course in Bangalore and workshops are conducted across all collages. ICSS had been fortunate enough to have been associated with some of the renounced educational institutions like IIT Kharagpur, NIT Durgapur, Jadavpur University, Lovely Professional University and JIS collage to name a few. Our campus representatives are highly active and conduct interactive sessions on cyber security. Campus representatives are student’s representatives from different collages those who are responsible for establishing a research lab on cyber security inside the campus of the respective collages. These research facilities & interactive sessions on ethical hacking helps the students to gain latest knowledge in cyber security. Indian Cyber Security Solutions offers Cyber security course in Bangalore for corporate teams and individuals.

Ethical Hacking Certification in Bangalore: Secure Your Digital World
Ethical Hacking Certification in Bangalore at Indian Cyber Security Solutions (ICSS), is a perfect opportunity to turn your curiosity into knowledge. We offer comprehensive training that gives you the skills and knowledge you need to succeed in ethical hacking. Our curriculum has been designed by industry experts, ensuring that you receive the most up-to-date and relevant training.
With our ethical hacking certificate course in Bangalore, you will dive into the intricacies of ethical hacking and explore the various techniques, techniques and tools used by cyber security professionals. Our experienced industry instructors will guide you through practical hands-on activities, real life case studies and intervention projects. By actively participating in these activities, you gain practical knowledge that prepares you for real situations.
At ICSS, Ethical Hacking Certification in Bangalore we understand the importance of a solid foundation in ethical hacking. That’s why our ethical hacking training in Bangalore is designed to give you the skills and knowledge you need to excel in this rapidly growing industry. Our instructors, with 12+ years of experience in the Networking field, bring a wealth of knowledge and industry insight to the classroom.
They are not only trainers but active professionals in the cyber security industry, ensuring that you receive useful, relevant and up-to-date training. Our ethical hacking training in Bangalore goes beyond technical skills. We focus on enhancing your corporate awareness, helping you create an impressive resume, and honing your communication skills. In addition, we offer regular assessments and individual attention to monitor your progress and address any specific learning needs you may have.
By the end of the Ethical Hacking Certification in Bangalore, you will have the confidence and knowledge to make a practical career in ethical hacking, protecting organizations from cyber threats and making a meaningful impact on cyber security Join our ethical hacking certificate course in Bangalore at ICSS and embark on a transformative journey to become an ethical hacking expert. Protect your future and make a difference in the cybersecurity landscape. Register today!
Why to Choose Ethical Hacking Certification in Bangalore, Karnataka
If you are looking for an ethical hacking certification in Bangalore, Karnataka, look no further than Indian Cyber Security Solutions. Located in the bustling city of Bangalore also known as Bangalore, our organization offers a comprehensive training program that equips aspirants with the skills and knowledge they need to excel in ethical hacking in.
As the capital and largest city of Karnataka, Bangalore is a hotbed of industrial growth and opportunity. As one of India’s most productive cities, Bangalore contributes significantly to the country’s IT exports, accounting for 38% of India’s total IT exports in 2014. The city’s IT industry is temperatures, and pleasant year-round weather , make it ideal for individuals exploring a career in ethical hacking.
At Indian Cyber security Solutions, we offer rigorous ethical certification courses covering all aspects of ethical hacking and cybersecurity. Our curriculum is designed to provide in-depth knowledge and practical skills through hands-on training, real-life scenarios and industry-related projects. By focusing on blended learning, we ensure that our students acquire the most practical skills to deal with hacking scenarios and understand the mindset of hackers.
During the course, students will have the opportunity to explore and apply their skills in a safe and controlled environment. Our experienced instructors, who are industry experts with years of experience in cyber security, give each student the right perspective and guidance. We also ensure individual attention through regular assessments
Do you want to be a Campus Representative?
If you want to be a CR there is a long list of benefits that you will be entitled too

Collages where we have conducted cyber security & ethical hacking training session
Workshop on Cyber Security at Ambedkar Institute of Technology
Indian Cyber Security Solutions conducted Workshop on Cyber Security at Ambedkar Institute of Technology. As mission of ICSS is to make digital India hack proof, we are on continues efforts to build a team of ethical hackers. The goal of this workshop is to spread cyber awareness. Eminent speakers from the industry demonstrated LIVE Hacks in the webinar. Nearly 350+ Students joined the webinars.