Diploma in Cyber Security Training in Hyderabad with Placement by Indian Cyber Security Solutions
Diploma in Cyber Security Training in Hyderabad by Indian Cyber Security Solutions provides a comprehensive curriculum covering network security, ethical hacking, incident response, cryptography, and more. This 12-month program combines theoretical knowledge with practical, hands-on experience, ensuring students are well-prepared for real-world cyber threats. With access to industry-leading tools and expert mentorship, both beginners and experienced professionals can advance their cybersecurity careers. The course enhances technical skills and boosts confidence to tackle cybersecurity challenges effectively. Enroll today to become an industry-ready cybersecurity professional, equipped with the skills that employers demand. Join ICSS in Hyderabad and secure your digital future.
Diploma in Cyber Security Training in Hyderabad focuses on core issues of cloud and network security. Starting with the basics and advancing to complex industry-level security problems, this training addresses crucial cybersecurity aspects. It involves protecting access to files and directories in a computer network against hacking, misuse, and unauthorized changes. With employment of information security analysts projected to grow by 18 percent from 2016 to 2024, this training provides in-depth knowledge on protecting networks, websites, and critical IT assets. Join us to build a career in this dynamic field. ICSS's Diploma in Cyber Security Training in Hyderabad is in high demand for its best practices against various cyber attacks, ensuring students are equipped to safeguard systems effectively.
Diploma in Cyber Security Training in hyderabad, designed by experienced penetration testers with over 15 years of experience, is your gateway to a rewarding job in cybersecurity. This comprehensive diploma signifies deep understanding and commitment, making you stand out to employers. Indian Cyber Security Solutions offers a robust framework, equipping you for roles like penetration tester or cybersecurity expert.











With attractive packages and promising career growth, our graduates are making significant strides in the industry. The images of our placed students, along with their impressive packages, highlight the real-world impact of our comprehensive training program.
Our recent placement records speak volumes about the success of our Diploma in Cyber Security Training in Hyderabad. At Indian Cyber Security Solutions (ICSS), we pride ourselves on providing top-notch education that prepares students for the demanding cybersecurity job market. Our students have secured prestigious positions in leading MNCs such as Wipro, TCS, Amazon, and many more.










Join our Diploma in Cyber Security Training in Hyderabad and take advantage of our strong industry connections and proven placement track record. Secure your future with ICSS and become a part of the elite group of cybersecurity professionals who are shaping the future of digital security.
Diploma in Cyber Security Course in Hyderabad
Diploma in Cyber Security Course in Hyderabad by Indian Cyber Security Solutions is in high demand. This comprehensive course teaches the most effective steps to prevent attacks and detect adversaries with actionable techniques. ICSS provides training from cybersecurity professionals, covering foundational, intermediate, and advanced security skills through industry-leading certification courses. The program starts with introductory-level training and progresses to advanced technologies like reverse engineering and penetration testing techniques. The Diploma in Cyber Security Training in Hyderabad is crucial for every team in every business, ensuring robust protection against cyber threats. Join us to advance your cybersecurity skills and secure your digital future.
Diploma in Cyber Security Course in Hyderabad by Indian Cyber Security Solutions addresses the critical need for cybersecurity expertise. According to the 2018 Cost of Data Breach Study by IBM, the global average cost of a data breach is $3.62 million. While hacking skills can be misused, our training teaches you to use these skills to protect organizational and individual intellectual property, becoming a white hat hacker. You will learn to measure and mitigate threats, identifying vulnerabilities within your organization. Many of our students have found Zero-day vulnerabilities. Enroll in our Diploma in Cyber Security Training in Hyderabad to build a successful career in cybersecurity and make a significant impact.
Diploma In Cyber Security Course in Hyderabad offered by Indian Cyber Security Solutions is a comprehensive program designed to equip individuals with the necessary knowledge and skills to excel in the field of cybersecurity. With a focus on practical training and industry-relevant curriculum, this course is ideal for both beginners and experienced professionals seeking to enhance their cybersecurity expertise. This course covers a wide range of topics, starting from the fundamentals of cybersecurity to advanced concepts such as network security, web application security, ethical hacking, and digital forensics. The curriculum is carefully designed to provide a step-by-step learning approach, ensuring that students understand each concept thoroughly before moving on to the next. One of the key advantages of the Diploma In Cyber Security Training in Hyderabad is the expertise of the faculty. The instructors at Indian Cyber Security Solutions are experienced professionals with in-depth knowledge and practical experience in the field of cybersecurity. They bring their industry experience into the classroom, providing real-world insights and practical examples to enhance the learning experience. So if you are looking for Diploma In Cyber Security Course in hyderabad, ICSS’s is your first preference.
The course also emphasizes hands-on training and practical exercises, allowing students to apply their knowledge in real-world scenarios. The institute provides well-equipped computer labs with the latest tools and software necessary for cybersecurity training. This enables students to gain practical experience in using industry-standard cybersecurity tools and techniques. By enrolling in the Diploma in Cyber Security Training in hyderabad, students not only gain theoretical knowledge but also have the opportunity to work on real-world projects and case studies. This practical exposure helps them develop problem-solving skills and enhances their understanding of the concepts learned in the classroom. It also prepares them to tackle real-world cybersecurity challenges effectively. One of the key advantages of the Diploma in Cyber Security Course in Hyderabad is the expertise of the faculty. The instructors at Indian Cyber Security Solutions are experienced professionals with in-depth knowledge and practical experience in the field of cybersecurity. They bring their industry experience into the classroom, providing real-world insights and practical examples to enhance the learning experience.
Indian Cyber Security Solutions offers a Diploma in Cyber Security Certification in Hyderabad, providing an exceptional opportunity for those seeking a career in cybersecurity. This program prepares you for the growing demand in the field, offering industry-recognized certification upon completion. With assistance in job placement and partnerships with top cybersecurity firms, the certification opens doors to a wide range of global employment opportunities. Gain practical experience and industry recognition, making it a wise investment in your professional future in the digital world.
Indian Cyber Security Solutions & Indian Institute of Cyber Security

Diploma in Cyber Security Training Institute in Hyderabad
2024 Ongoing Campus Placement
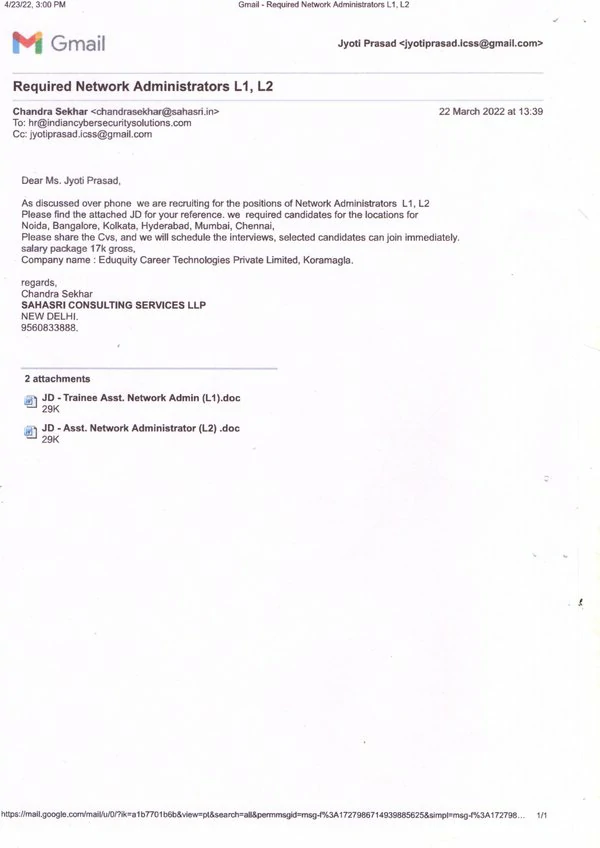
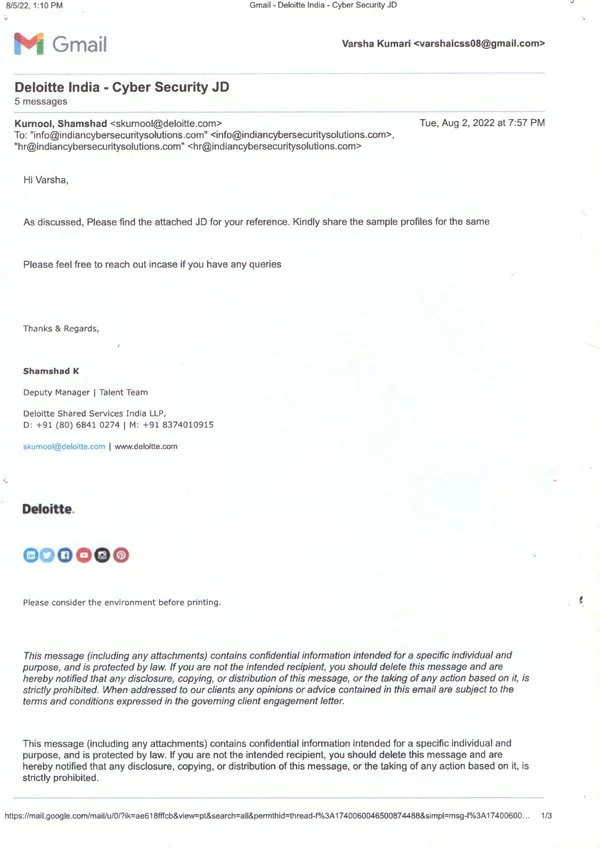
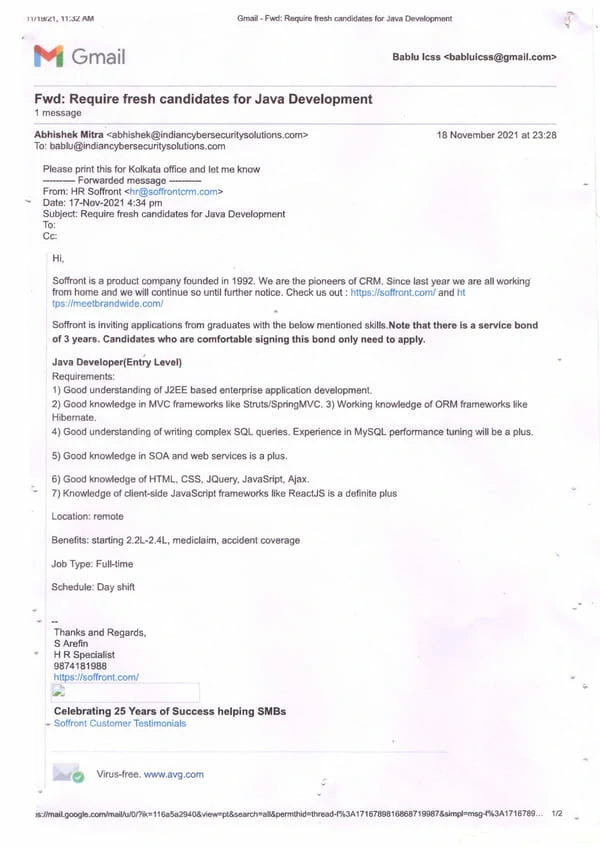
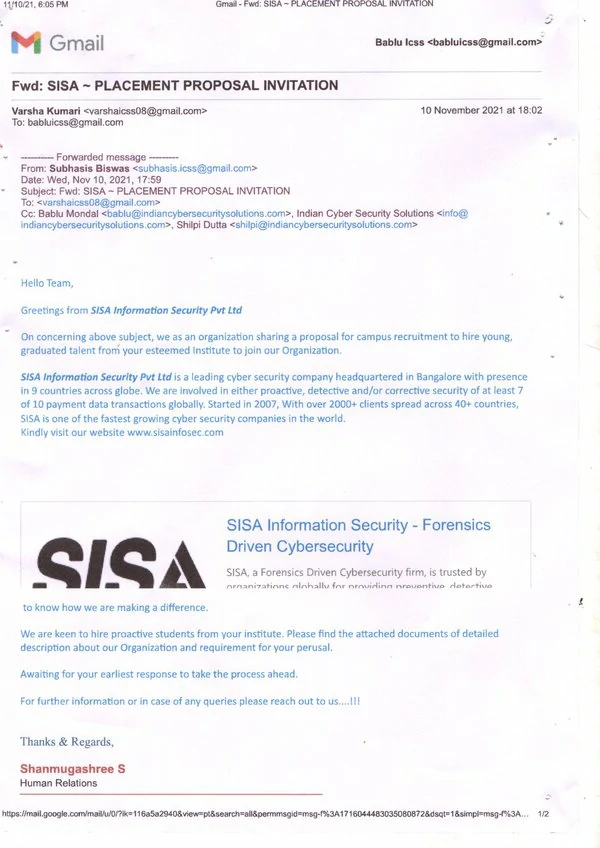
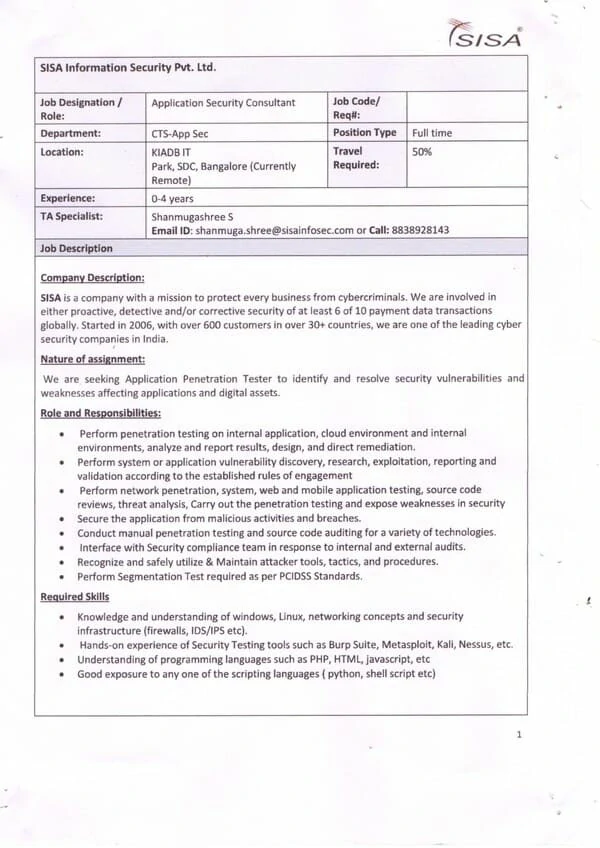
Diploma in Cyber Security Training Institute in Hyderabad: Indian Cyber Security Solutions (ICSS) stands out as the premier destination for cybersecurity education. Diploma in Cyber Security Training in Hyderabad is strategically positioned in the heart of the city, our office is easily accessible, ensuring seamless connectivity for students from all parts of Hyderabad. Located in HITEC City, the IT hub of Hyderabad, ICSS offers unparalleled advantages for aspiring cybersecurity professionals. HITEC City is renowned for its thriving tech ecosystem, hosting numerous IT companies and startups. This vibrant environment translates to increased on-campus placement drives, providing our students with direct access to potential employers. The supporting emails from companies participating in our campus recruitment programs testify to the success of our placement initiatives. Join ICSS in Hyderabad and leverage the advantages of being at the center of the tech industry to advance your cybersecurity career.


Diploma in Cyber Security Training Institute in Hyderabad: For students, finding affordable accommodation is hassle-free. Our institute is conveniently located in HITEC City, surrounded by numerous budget-friendly housing options. This proximity not only reduces commute time but also enhances the overall learning experience by fostering a conducive living and studying environment. Our Diploma in Cyber Security Training in Hyderabad is designed to meet the highest industry standards, ensuring that students are well-equipped with the skills and knowledge demanded by employers. The comprehensive curriculum covers critical areas such as ethical hacking, network security, and incident response, making our graduates highly sought after in the job market. Join ICSS and take the first step towards a successful career in cybersecurity. Experience the benefits of studying in Hyderabad’s prime IT location, with ample placement opportunities and affordable living options. Transform your career with our Diploma in Cyber Security Training and become a part of the elite group of cybersecurity professionals.
Since 2016, Indian Cyber Security Solutions (ICSS) has become the leading Diploma in Cyber Security Training Institute in Hyderabad. Our program is designed to equip students with the skills needed to excel in the cybersecurity field. With a strong emphasis on practical, hands-on training, our graduates are well-prepared for the challenges of the industry.
ICSS boasts a stellar placement record, with students securing positions in prestigious companies like Wipro, TCS, and Amazon. Located in Sector V, Kolkata's IT hub, we provide students with excellent opportunities for networking and on-campus recruitment.
Our success over the years is a testament to our commitment to quality education and student success. Join ICSS and become part of a legacy of excellence in cybersecurity training. Enroll in our Diploma in Cyber Security Training Institute in Hyderabad today and take the first step towards a promising career. Visit our website to learn more and register now!