Diploma in Advanced Cloud & Network Security by ICSS
Diploma in Advanced Cloud & Network Security from Indian Cyber Security Solutions is the best part. A recent study showed that 90% of breaches are caused by employee carelessness. If a program is implemented to teach them about common scams, such as email attachments that contain malware or phishing emails that steal personal information, they are much less likely to accidentally click links or open files. As cyber-crime continues to wreak havoc, regulations continue to be implemented to protect data. Having a strong security policy coupled with security awareness training means less worrying. Cybersecurity professionals work in every size company and industry to protect organizations from data breaches and attacks. After completion of Diploma in Advanced Cloud & Network Security from Indian Cyber Security Solutions, you can build your career in the cybersecurity field. As a cybersecurity expert, you will have a huge range of career options across a wide variety of industries.
Cyber-attacks are being reported every day, and it is becoming more important for organizations and businesses. Diploma in Advanced Cloud & Network Security by Indian Cyber Security Solutions focuses on the core issues of network security. Starting from the basics of networking and then core security problems faced by industry experts while working as a network security professional. Network security process of protection of the access to files and directories in a computer network. Against hacking, misuse and unauthorized changes to the system. The importance of cybersecurity practices, training, and systems isn’t isolated to private, internal business operations. The past two decades have seen both state and federal movements to draft cybersecurity regulations. Certain industries are affected by cybersecurity regulatory requirements more than others.

Indian Cyber Security Solutions is awarded the 2nd position as the
" 10 Most Promising Cyber Security Training Institute in India 2020 "
4.8 ( 21,123 ratings )
1,09,233 Students Enrolled
Eligibility Criteria for Diploma in Advanced Cloud & Network Security
Students from any background can apply for this course. We provide 18 Months of Hands-on training by Industry experts. They are real-time hackers and currently working in this domain. Advanced Cloud & Network Security Diploma Course in Kolkata course will help you to develop your necessary skills required in the industry. You will able to secure a job as a penetration tester after that.

It uses the same knowledge and tools as a malicious hacker but in a lawful and legitimate manner. It can assess the security posture of a target system. Securing a network requires a complex combination of hardware devices, such as routers, firewalls, and anti-malware software applications. Grow your knowledge in this field by the course.
Learn from Industry Experts & Get Real Hands-On Experience and get job ready

Get Started with FREE Demo Class:
* We don’t share your personal info with anyone. Check out our Privacy Policy for more info.
Why You Should Choose ICSS ?
Industry professions from Amazon, Cognizant & Intel will share their practical experience in the class
100% practical and lab-based classes (available online & offline)
25% Scholarship program for merited students with a minimum of 95% marks and above in their 12th board exams
LIFETIME access to video tutorials, case studies
EMI option is available if you go for 2 or more courses.
Get educational loan @ O% interest
TRAINING METHODOLOGY of ICSS
With our full Training Methodology you will get job

CCNA - Course Module
- What is a Computer network
- LAN
- MAN
- WAN
- Parts of network
- Network Fundamentals
- OSI model
- What is Modem?
- What is Router?
- What is Switch?
- What is Repeater?
- EXAM
- IP Connectivity
- How binary code works?
- What is Network ID?
- What is Host ID?
- Sub netting
- CIDR notation
- Variable Length Subnet Mask (VLSM)
- Verifying and troubleshooting in ip address
- Sub netting in Binary
- Create a Sub netting Cheat Sheet
- IP Connectivity
- What is TCP?
- What is UPD?
- What is HTTP?
- What is FTP?
- What is TFTP?
- What is SMTP?
- What is POP?
- What is ICMP?
- Ethernet
- IP Connectivity
- Cisco hardware components
- Cisco software
- Router categories
- Routers ports
- Router functions
- Ideal network Ideal network
- IP Connectivity
- How it decides best route?
- Static routing & CONFIGRURATION
- Dynamic routing
- IP Services
- Lecture-46: DHCP methods·
- Lecture-47: DHCP scope·
- Lecture-48: DHCP leased period
- Lecture-49: DHCP configuration parameters
- IP Services
- Lecture-43: Static NAT configuration
- Lecture-44: Dynamic NAT configuration
- Lecture-45: NAT overload configuration (PAT)
- IP Services
- Introduction to SNMP
- SNMPv2
- SNMPv3
- IP Connectivity
- Default Gateway
- Administrative Distance
- Introduction to Route Summarization
- IP Connectivity
- Static Routing
- IP Routing Explained(default )
- IP Routing Explained (next hop address)
- IP Routing Explained (serial port)
- Floating Static Route
- IP Connectivity
- Introduction to OSPF
- OSPF Configuration
- OSPF Packets and Neighbor Discovery
- OSPF Reference Bandwidth
- OSPF Router IDOSPF DR/BDR Election
- OSPF Passive Interface
- OSPF Hello and Dead Interval
- IP Connectivity
- Lecture 68: priority
- Lecture 69: pre-emption
- Lecture 70: version
- Lecture 71: Configuration HSRP
- First Hop Redundancy Protocols – GLBP
- Network Access
- Introduction to VLANs
- How to configure VLANs
- VLAN Trunking Protocol (VTP)
- Introduction to 802.1Q
- How to configure a Trunk
- Dynamic Trunking Protocol (DTP)
- 802.1Q Native VLAN
- Introduction to Voice VLAN
- EtherchannelsL3 Etherchannel
- Network Access
- Introduction to Spanning-Tree
- Per VLAN Spanning-Tree
- Spanning-Tree Port States
- Spanning-Tree Cost Calculation
- Spanning-Tree Portfast
- Rapid PVST
- Rapid PVST Configuration
- Network Access
- Introduction to Wireless Networks
- Introduction to Wireless LANs
- Wireless LAN 802.11 Service Sets
- Introduction to Wireless Security
- Wireless Authentication Methods
- Wireless Encryption and Integrity
- Wi-Fi Protected Access (WPA)
- Cisco Wireless Network Architectures
- Cisco WLC Deployment Models
- Cisco Wireless AP Modes
- Cisco Wireless LAN Controller (WLC) Basic Configuration
- Cisco WLC WPA2 PSK Authentication
- What is
- Directory Listing
- Live Demo on
- Directory Listing
- What is
- Broken Auth
- Live Demo on
- Broken Auth What is
- Tamper data?
- Live Demo on
- Tamper Data on Ecommerce site
- Session Hijacking
- QUESTION ANSWER & DISCUSSION + EXAM
- IP Connectivity
- Introduction to IPv6
- Shortening IPv6 Addresses
- How to find IPv6 Prefix
- IPv6 Address Types
- IPv6 Address Assignment Example
- IPv6 EUI-64
- IPv6 Summarization
- IPv6 Solicited Node Multicast Address
- IPv6 Neighbor Discovery Protocol (NDP)
- IPv6 Stateless Auto configuration
- Security Fundamentals
- Introduction to Access-Lists
- Wildcard Bits
- Standard Access-List
- Extended Access-List
- Time-based Access-List
- Security Fundamentals
- Port-Security
- AAA and 802.1X
- AAA User Authentication
- AAA Admin Authentication
- DHCP Snooping
- Introduction to Firewalls
- Introduction to VPNs
- Introduction to CDP
- Introduction to LLDP
- Telnet Server and Client
- SSH Server and ClieT
- Introduction to NTP
- Introduction to Syslog
- Configuration Register
- Password Recovery on Cisco IOS
- Cisco IOS File System
- Upgrade Cisco IOS Image
- Device Programmability
- REST API
- Data Models and Structures
- Configuration Management Tools and Version Control Systems
- Introduction to Software Defined Networking (SDN)
- Spine and Leaf Architecture
- Virtual Machines and Containers
- Introduction to Cloud Computing
- Cloud Connectivity
CCNP - Course Module
- Route Summarization
- Redistribution concepts
- Redistribution between EIGRP & OSPF
- Prefix List
- Distribute List
- Route Map
- EIGRP concepts
- Metric calculation
- Eigrp classic & named mode configuration
- EIGRP Authentication
- Unequal cost Load balancing
- Variance multiplier configuration
- Eigrp Summarization
- OSPF multiarea
- DR & BDR
- OSPF Authentication
- OSPF summarisation
- OSPF LSA types
- OSPF Area types: Stub, Totally Stub, NSSA, NSSA Totally Stub
- OSPF Virtual Link
- OSPF Path Selection
- OSPF network types
- OSPF v3 configuration
- Border Gateway Protocol (BGP) concepts: IBGP || EBGP
- BGP configuration
- BGP path selection attributes: AS-PATH Local Preference Weight
- Multiprotocol BGP
- BGP Route Reflector
- VPN GRE
- DMVPN
- MPLS
- VXLAN
- LISP
- Redundancy protocols- HSRP || GLBP
- NAT /PAT
- NTP
- Wireless Networking
- Wireless Security standards
- Quality Of Service
- Access Control List
- Telnet& SSH
- AAA Authentication
- SYSLOG
- Control Plane Policing
- Software Defined Networking (SDN)
- Cloud computing models
- Virtualization
- Automation Device models & structure
- REST API
- Device Programmability
- Automation using Ansible
- Implementing Multicast using IGMP
- Switch Loop Avoidance STP RSTP MSTP
Amazon Web Services (Basic & Advance) - Course Module
- What is Cloud Computing
- Advantages of Cloud Computing
- Industry definition
- Software & Hardware Enablement
- Service Models
- Deployment models
- AWS Certification Track
- AWS Global Infrastructure (Regions, Availability Zones & Edge Locations)
- Signing Up for AWS – AWS Free Tier and Account sign up
Service Overview
Instance: Types and classes
Instance: Attributes and Pricing
Launching your first AWS Linux and Windows instance
How to Access Both Instance (SSH and RDP)
Launch Templates
Key Pairs, Security Groups
Placement Groups
- Service Overview, Types and Pricing
- How to Extend Volume Size Runtime
- Introduction to Snapshots
- Detach and Terminating EBS volume
- Restore Volume Data from Snapshot
- Creating and Deleting Snapshots
- How to Share Volume between different instances in different AZ
- EBS Snapshot Copy between Region
- Creating volumes from Snapshot
- EBS Volume Pricing
- Snapshot Lifecycle Policy & DLM
- Choosing the AMI (AWS, community, custom)
- Copy and Share AMI across Regions and Accounts
- Creating a new AMI from existing Instance·
- Deploying a new Instance from the custom AMI
- Introduction to Load Balancing, target groups
- Service Overview, Pricing
- Type of Load Balancers
- Creating an Elastic Load Balancer
- Create an ELB with Web Servers across availability Zones
- Service Overview and Pricing
- Setting up an Auto-scaled, Load-balanced Amazon EC2 application servers
- Understand Launch configurations and Launch Groups
- Service Overview and Pricing
- VPC Components overview: Route Table, Subnet, DHCP Options Set, NACL
- Create custom VPC for practical implementation in coursework
- Elastic IPs, Public IPs and Private IPs
- Elastic Network Interface (ENI) and EC2
- Internet Gateway (IGW), Security Group (SG)
- Setup VPC Peering connection
- Service Overview and Pricing
- Creating Users, Groups and Roles
- Creating User and Group policies
- Configure Custom Policy
- Setup Password Policy
- Activating MFA for a user
- Creating custom identities and roles for restricted access
- Service Overview and Pricing
- Logs and Metrics
- Create custom logs, dashboards
- Create custom Cloudwatch Alarms and validate
- Service integration with EC2
- Service overview and Pricing
- SNS Protocols
- Creating and subscribing to SNS topics
- Service integration with CloudWatch
- Service Overview and Pricing
- EBS vs EFS vs S3
- How to Access S3 Bucket and upload / download / access data
- S3 Static Website Hosting
- S3 Permissions and Bucket policies
- Life Cycle of Object & S3 Versioning
- Enable Server Access logging
- Understand Storage Classes
- Service Overview and Pricing·
- Essential concepts
- Create Lambda Applications (Node.js)
- Create custom Lambda functions (Python)
- Concurrency
- Service Integration with S3
- Service Overview and Pricing
- RDS instance types
- Creating and managing Databases (MySQL/MariaDB implementation)
- Setting up automatic backups, snapshots & restores
- Service integration with EC2
- Service Overview
- Setup local environment for CLI access
- Manage AWS resources with AWS CLI from local environment
- Service implementation with S3 and EC2
- Service Overview
- Stacks & Stack Sets
- Deploy Cloud Formation Stack (Lab)
- Understand Designer principles and IaaC concepts
Bills
Cost explorer
Consolidated Billing
RHCE Training
C|EH v11 - Course Module
- What is Hacking
- What is Ethical Hacking
- Types of Hackers
- White Hat Hacker
- Black Hat Hackers
- Gray Hat Hackers
- Script Kiddies
- Hacktivists
- Spy Hackers
- Cyber Terrorists
- Vulnerability
- Exploit
- Remote Exploit
- Local Exploit
- Zero-day
- Zero-day vulnerability
- Zero-day Exploit
- Brute force attack
- Phishing
- Remote access
- Payload
- Active Information Gathering
- Passive Information Gathering
- Scanning
- Gaining Access
- Maintaining Access
- Covering Tracks
- Viruses
- Worms
- Trojan Horse
- Spyware
- Adware
- Backdoor
- Rootkits
- Ransomware
- What is Penetration Testing
- Types of Penetration Testing
- What is white box Penetration Testing
- What is Black Box Penetration testing
- Introduction to Linux OS
- Social Engineering
- What is Virtual Machine
- What is VMware
- What is Virtual Box
- Install VMware
- Install Kali Linux
- Install Windows XP
- Install Windows 7
- Install Windows 10
- Install Add on in Mozilla
- Tamper Data
- Burp Suite
- No-Redirect
- Install Nessus
- QUESTION ANSWER & DISCUSSION + EXAM
- System Hacking
- using Kon-Boot
- EFI and Secure Boot feature
- Network Scanning
- Port Scanning
- Service Scanning
- What is Nmap
- Scanning With Nmap
- Nmap Various Command
- QUESTION ANSWER & DISCUSSION + EXAM
- What is Metasploit?
- Xp Remote Exploit using Metasploit
- Msfvenom
- Windows 7 UAC Bypass
- QUESTION ANSWER & DISCUSSION + EXAM
- SE-Toolkit Usages
- Exploit With SE-Toolkit
- What is RAT
- Exploit With RAT
- Protect System from RAT
- Types of Sniffing
- Network Sniffing with Wireshark
- Get FTP Login Details Using Wireshark
- QUESTION ANSWER & DISCUSSION + EXAM
- Details of DOS
- What is DDOS
- Encryption Hacking Wireless Network
- QUESTION ANSWER & DISCUSSION + EXAM
- How Web Application Works
- Request and Response
- Installing Scanner (Acuntix,Netsparker)
- Scanning Website
- QUESTION ANSWER & DISCUSSION + EXAM
- Types of Sql-Injection
- Live Demo on Sql-Injection
- QUESTION ANSWER & DISCUSSION + EXAM
- Types of XSS
- Live Demo
- on XSS All types
- QUESTION ANSWER & DISCUSSION + EXAM
- What is CSRF
- LiveDemo On CSRF
- What is HTML Injection
- Live Demo on
- HTML Injection
- QUESTION ANSWER & DISCUSSION + EXAM
- What is
- Directory Listing
- Live Demo on
- Directory Listing
- What is
- Broken Auth
- Live Demo on
- Broken Auth What is
- Tamper data?
- Live Demo on
- Tamper Data on Ecommerce site
- Session Hijacking
- QUESTION ANSWER & DISCUSSION + EXAM
- What is
- Phishing?
- Create a Phishing Page
- What is Web
- Shell
- Hack Web-Server
- Using Web-Shell
- QUESTION ANSWER & DISCUSSION + EXAM
- Hacking Android Phone using Metasploit
- QUESTION ANSWER & DISCUSSION + EXAM
- IOT & OT concepts
- IOT & OT Attacks
- IOT & OT Hacking Methodology
- Countermeasure
- IOT & OT Pentesting
- Cloud Computing Concepts
- Cloud Computing Threats
- Cloud Computing Attacks
- Cloud Security
- Cloud Security Tools
- Cloud Penetration Testing
- Cryptography Concepts
- Encryption Algorithms
- Cryptography Tools
- Public Key Infrastructure
- Email Encryption
- Disk Encryption
- Cryptanalysis
- Countermeasures
C |NPT - Course Module
- Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources.
- According to the configuration of Laptop, 32/64 bit, provide VMware, and any Penetration testing OS like Kali/Parrot, Windows XP SP3, Windows 7
- Active Information Gathering in depth, Passive Information Gathering in depth, Sniffing, Vulnerability Scanning
- Exploiting Windows and Linux System
- Application of Metasploit
- Creating malicious files (standalone binaries) using msfvenom
- Remote Exploit
- Evading Antivirus
- Uac Bypass
- Exploiting using different File Format
- Post Exploitation
- Here students will learn how to hack a android device and get details out of it.
- Studying ARP, how it works and how it can be manipulated to mount sophisticated attacks is made extremely easy to understand. Sniffing is a technique that you will be able to fully grasp in its most practical aspects. We will make sure you have enough basics of network theory before we cover actual attack scenarios using the best tools available. Man in the middle attacks are one of the most used penetration testing techniques today; you will be able to mount man in the middle attacks within local networks and over the Internet.
- Penetration testers rarely need to cover their tracks. However there are times when testing the efficiency of the target organization incident response team is within the scope of a Penetration tester’s engagement.
- Social engineering module will guide you through the most modern social engineering attack techniques. Real world attacks will be illustrated by exploiting the potential of social networks such as Facebook, Spokeo or Twitter. Almost one hour of video lessons will teach you everything you need to know to master the most important tool in the field: Social Engineering Toolkit.
- The following module focuses on the attacks that can be executed on Wi-Fi networks. The student will learn how to attack and access remote Wi-Fi networks, obtain keys, password and much more, according to their configuration and security mechanism. We will first start exploring the attacks against WEP and then focus our tests on more secure networks: WPA, WPA2 and WPS.
- In the last module, of the Wi-Fi section, the student will learn how to use Wi-Fi as an attack vector. This means that we will not attack Wi-Fi networks, instead we will use Wi-Fi in order to create fake networks, obtain credentials, run MitM attacks and much more.
Class Room Training
Course Fee
Classroom with global - INR 93,000/- + 18% GST
Course Duration - 40 Hours
18 Months Training
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Online Self Paced LIVE Training
Course Fee
Online Course Fee - INR 91,000/- + 18% GST
Course Duration - 40 Hours
18 Months Training
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Gradation System (on total marks obtained)
GRADE | PERFORMANCE | PERCENTAGE |
|---|---|---|
E | Outstanding | 90% – 100% |
A+ | Excellent | 80% – 89% |
A | Very Good | 70% – 79% |
B+ | Good | 60% – 69% |
B | Poor | 50% – 59% |
C | Not Qualified | Reappear all the modules |

After successful completion of the training and exam, you will receive a certificate from Indian Cyber Security Solutions which is recognized by all the companies in India.
Do check out the sample certificate: CLICK HERE
Achievements of our Students
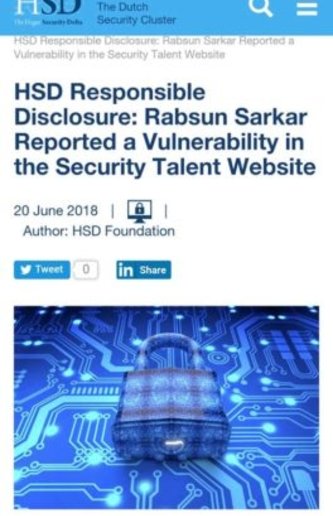
Many of our students have founded Zero-Day Vulnerabilities and also their CVE has published on Exploit-DB. Check their CVE and also read their Blog on Exploit DB.
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
RECENT PLACEMENTS
Need to Work on real-time projects and complete assignments to get Professional Certification from Indian Cyber Security Solutions
ICSS provides the course completion certificate once you successfully complete the Certified AWS Training program Professional Certificate Holders work at 1000s of companies like HP, TCS, Amazon, Accenture, Microsoft and many more.
REGISTRATION DESK
Still Hunting for a Job? or Want to Make a Career Switch into
Cyber Security?
Recruiters are looking for you!
Become Certified Professional and Get JOB with our Free Placement Assistance Program
Diploma In Advanced Cloud & Network Security conducted by Indian Cyber Security Solutions
Diploma In Advanced Cloud & Network Security, ICSS is a great opportunity for interested people to grow their careers in the Cyber Security industry. They can join immediately at Indian Cyber Security Solutions for Diploma in Web Application Security internet continues to advance, cybercrimes increasing as well. Criminals can commit crimes easily with a few clicks. Current technology has given us assess to huge amounts of information on the web and mobile devices. It has simplified tasks like shopping, paying bills, and banking services. It has also given rise to the need for ethical hackers to battle cyber criminals.
How you can get priority in Job Placement after doing the course from ICSS?
There is no better time than now to begin a career in the cybersecurity industry. In fact, candidates who will accomplish a Diploma In Advanced Cloud & Network Security can get career opportunities with high pay scales. Indian Cyber Security Solutions had trained more than 1298+ students and is proud to be the best Diploma In Advanced Cloud & Network Security. With around 20+ penetration testers and ethical hackers working with Indian Cyber Security Solutions, it is quite easy to provide world-class practical training which is required for the certification. From the Diploma In Advanced Cloud & Network Security, you will be able to improve your knowledge of risks and vulnerabilities and learn how to think like a hacker.
After that course, it will boost your salary and advance your security career. You will learn to use the real hacking tool. Cybercriminals are innovators and will constantly discover new ways to attack IT infrastructure and exploit vulnerabilities. Without knowledge of the risks and vulnerabilities associated with your computer systems, you will have a difficult time keeping them secure. ICSS confirms by their course of Diploma In Advanced Cloud & Network Security the capacities of an ethical hacker to prepare for vulnerabilities of system foundation and prevent illegal hacking.
Do you want to be a Campus Representative?
If you want to be a CR there is a long list of benefits that you will be entitled too.