Capture The Flag Training in Bangalore(CTF Training in Bangalore) |- ICSS
Capture The Flag Training in Bangalore is a global certification that is valid in more than 160 countries. We are an authorized training partner of the EC Council for the last 10 years. We have a pool of professional certified ethical hackers who are working as security analysts in different organizations. Capture The Flag Certification in Bangalore from the ICSS provides the gateway to enter the cybersecurity domain. MNCs have made Capture The Flag certification compulsory for security-related jobs. Get the Capture The Flag Certification course in Bangalore from the Best Capture The Flag Training Institute in Bangalore.
What is Capture The Flag?
Capture the Flag is an information security competition that is an amalgamation of various challenges that applies concepts like Reverse engineering, Web Applications, Binary, Network, Cryptography, Forensics, etc. Each challenge holds a certain number of points based on its difficulty level. The idea behind these Capture The Flag is to provide an individual practical knowledge of the different kinds of attacks and issues in the real world. For aspiring white hats, Capture The Flag challenges are a good thanks to learning hacking techniques, strengthen your problem-solving skills, and gain critical hands-on practice. Capture The Flag competitions deal with the correct level of pressure to stay things interesting while helping you to sharpen your skills. For the pros, Capture The Flag competitions facilitate your assess your skill level, challenge yourself among peers, and perhaps even earn some bragging rights.

Indian Cyber Security Solutions is awarded the 2nd position as the
" 10 Most Promising Cyber Security Training Institute in India 2020 "
In computer security Capture the Flag (CTF), "flags" are secrets hidden in purposefully-vulnerable programs or websites. Competitors steal flags either from other competitors (attack/defense-style CTFs) or from the organizers (jeopardy-style challenges).
A cybersecurity capture the flag is a team-based competition in which participants use cybersecurity tools and techniques to find hidden clues or “flags”. The team that locates the most flags during the event wins. These events are often entry-level and open to the public.
When a player is in an opposing team's territory, they can be captured by that team's players. If they tag the player, the player must perform a task—say, five jumping jacks or three push-ups—before returning to their own territory.
Capture the Flag (CTF) is a special kind of information security competitions. Well, attack-defence is another interesting kind of competitions. Here every team has own network(or only one host) with vulnarable services. Your team has time for patching your services and developing exploits usually.
One of the CTFs that was particularly interesting to me was the Google CTF. One can opt to go for the beginner challenges to see where the skill level really was at - and although it is “mostly” easy, there are still some challenges that can make the competition tough.
CTFs enable you to develop your problem solving and analytical skills to use in real-work scenarios. CTF tasks are usually based on real-world vulnerabilities and security incidents. Nowadays, CTF problems are asked in job interviews to test the skills of professionals.

Capture The Flag Training Institute in Bangalore
ICSS being the best Capture The Flag Training Institute in Bangalore, will build your knowledge of the tools and techniques used by hackers. As a result, you will learn how malicious hackers use various tools. This certification is highly demanded by top companies as a prerequisite for information security-related job posts. So you should explore to advance your career to the top position in security. Get ahead on your career with in-depth and intensive training for Capture The Flag certification in Bangalore.
Capture The Flag training in Bangalore with hands-on training in the lab from the professional hackers who are themselves CEHv10 certified, OSCP Certified. Cyber Security training is in huge demand as organizations are going online with more than 170 Billion Dollar investment in the cyber security domain worldwide. At Indian Cyber Security Solutions, you will learn in-depth on an attacker can hack an organization and also how the defend the intellectual property of the organization from being hacked. Capture The Flag Training in Bangalore is designed in such a way that you get the maximum practical knowledge within 40 hours of course module. At our training center, we bring in guest faculties from the industry so they can share their practical experience with you. At the end of the course, we aim to make you placement ready.
Indian Cyber Security Solutions have 130+ trainers who are professional CTF working in different MNCs like Infosys, Cognizant, Wipro, ATOS, Intel and are also members of our research & development team. All the trainers are geographically located in different areas provide online training on Ethical Hacking. All the CTF classes are held through an application where the faculty and the students are LIVE interacting with each other over the internet. All the classes are recorded and uploaded in our online portal “ HACKERS LAB “ where all students have lifetime access. We guarantee your satisfaction or we pay back your course fee. There will be 3 instructors dedicated to individual batch which will carry on for 3 months
Eligibility Criteria for Capture The Flag Course
Prior to opting for this course, the candidate should be aware of advanced ethical hacking techniques, networking services, OWASP top 10, Linux /Windows basic and major commands, the Unix File System and the working of the Content Management System.
Achievements of our Students
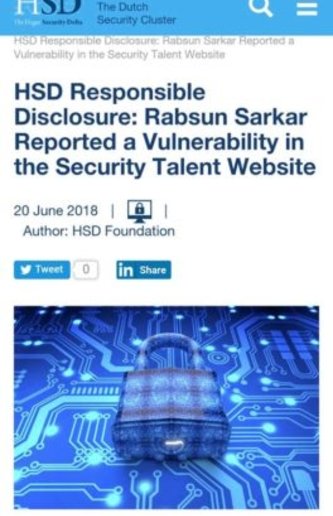
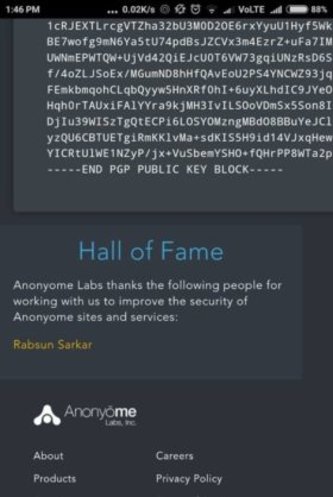
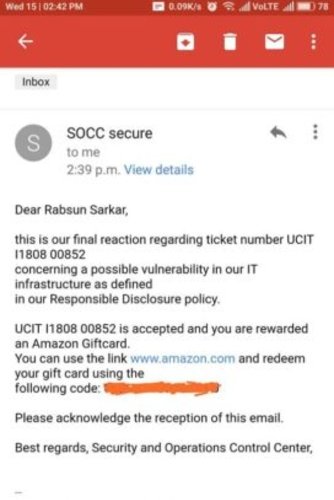
Many of our students have founded Zero-Day Vulnerabilities and also their CVE has published on Exploit-DB. Check their CVE and also read their Blog on Exploit DB.
Rabsun Sarkar one of our students has found zero-day vulnerabilities in Google and in the Security Talent Website and also reported for the same.
Learn from Industry Experts & Get Real Hands-On Experience and get job ready

Get Started with FREE Demo Class:
* We don’t share your personal info with anyone. Check out our Privacy Policy for more info.
Why You Should Choose ICSS ?
Industry professions from Amazon, Cognizant & Intel will share their practical experience in the class
100% practical and lab-based classes (available online & offline)
25% Scholarship program for merited students with a minimum of 95% marks and above in their 12th board exams
LIFETIME access to video tutorials, case studies
EMI option is available if you go for 2 or more courses.
Get educational loan @ O% interest
TRAINING METHODOLOGY of ICSS
With our full Training Methodology you will get job

JOB ORIENTED CAPTURE THE FLAG TRAINING COURSE DETAILS
100% Job Placement Assistance
- Career Guide: Job Opportunities will be shared with you
- Be JOB Ready Resume prepared by Experts
- Questions & Answers provided for interviews
- Mock Exams you will write to test your skills
- Mock Interviews to boost your confidence
- Pre-Requisite: Cyber Security Specialist
- Projects: Work on Real Life Case Studies
Course Duration
We Provide:
- 40 Hours Classes
- Fast Track Classes
- Weekdays & Weekend Classes
- In Class, You Get In-Depth ethical hacking Knowledge on each Topic
- Projects to do assignments
- Location: Courses are run in our Kolkata training center (Salt Lake, Sector 5) & Bangalore (Indiranagar)
- Corporate Training for your Employees
- Online CTF training Courses - Live Instructor LED Classes
- Pay only after attending FREE DEMO CLASS
CTF - Course Module
- Introduction to CTF and its importance in cyber world
- Introduction to Cyber Range
- Difference between CTF and Cyber Range
- CTF Course overview
- Types of CTF challenges platform
- Famous Channel Of CTF
- Basics of Linux service
- Linux foremost commands
- Linux filesystems
- Linux Utility
- Installing & configuration of systems packages
- Deleting & removing systems
- package
- Reading Logs
- Basics of Windows services & Registry
- Windows foremost commands
- Windows filesystems
- Windows Utility
- Working of dll, Python & C-programs
- Installing & configuration of systems packages
- Deleting & removing systems package
- Reading event Logs
- Introduction to toolbox
- Installing & configuring services
- Installing & configuring Kali tools
- Basic to Advanced Pen testing Commands
- Brute force Attack
- Hands-on Practice on
I. Nmap
II. Metasploit
III. SQLMAP
IV. Burp Suite
V. Wireshark | TCPDUMP
VI. Nikto
VII. Curl
VIII. Netcat
IX. wpscan
X. John the ripper
- TCP Connect Scan with Wireshark
- Network Sweeping with Wireshark
- SYN Scan with Wireshark
- UDP Scan with Wireshark
- FIN Scan with Wireshark
- Null Scan with Wireshark
- OS Discovery with Wireshark
- NSE Scripts with Wireshark
- Nmap Firewall Scan
- Overview
- DNS Enumeration
- NetBIOS & SMB Enumeration
- Enum4Linux
- SMB NSE Scripts
- MSQL Enumeration
- MSSQL Enumeration
- SMTP Enumeration
- VRFY Script
- Python Port
- SNMP Enumeration
- SNMP MiB
- SNMP Walk
- SQL Injection
- LFI & RFI
- Remote code | command Execution
- Authentication Bypass
- Directory Brute Forcing
- Nmap
- Google Hacking
- Searchploit
- Exploit DB
- Nessus
- Powershell Script
- SE-Toolkit Usages
- Exploit With SE-Toolkit
- Php reverse shell
- Python reverse shell
- Perl reverse shell
- Bash reverse shell
- Msfvenom shell
- Adding Exploit in Metasploit framework
- Manual Exploitation
- Using Python script
- Unicorn
- Buffer Overflow
- Overview
- Vulnerable Code
- Stack Overflow
- Overview
- Fuzzing
- Crash Replication
- Controlling EIP
- Introducing Shellcode
- Bad Characters
- Redirecting Execution
- Introducing Mona
- Shellcode Payload
- Overview
- Controlling EIP
- Locating Space
- First Stage Shellcode
- Locating RET
- Generating Shellcode
- Getting start with NC
- Connecting to a Server
- Fetching HTTP header
- Chatting
- Creating a Backdoor
- Verbose Mode
- Save Output to Disk
- Port Scanning
- TCP Delay Scan
- UDP Scan
- Reverse TCP Shell Exploitation
- Randomize Port
- File Transfer
- Reverse Netcat Shell Exploitation
- Banner grabbing
- Overview
- Port Forwarding
- SSH Tunnels
- Dynamic Proxies
- Proxy Chains
- FTP
- Python HTTP Server
- php http server
- HFS Tool
- Netcat
- CURL
- Wget
- TFTP
- Python SMB Server
- Powershell File Transfer
- Bitsadmin
- Jenkins
- Docker
- LXC
- WordPress
- Drupal | Joomla
- Writable Script
- Crontab
- Kernel
- Path Variable
- Automated Script
- Kernel
- Bypass UAC
- Unquoted Path
- Scheduled Task
- Automated Scrip
- Level -1: Easy
- Level-2: Medium
- Level-3: Intermediate
- Level-4: Hard
- Designing Jeopardy CTF Challenges
- Designing Attack & defense Challenge
a. CTF Classification
b. Cryptography
c. Steganography
d. Encoding
e. Binary
f. Pwn
g. Web
h. Network
- Designing Penetration Testingframework (PTF)
Class Room Training
Course Fee
INR 13,000 / - + 18% GST
Course Duration - 40 Hours
3 Months Training
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
Online Self Paced LIVE Training
Course Fee
INR 13,000 / - + 18% GST
Course Duration - 40 Hours
3 Months Training
2 Classes Per Week X 2 Hours Each Day
Batch Timing
Week End Classes | Week Days Classes
RECENT PLACEMENTS
Still Hunting for a Job? or Want to Make a Career Switch into CTF?
Recruiters are looking for you!
All you need to Learn Basic to Advance of CTF with ICSS, Become Certified Professional and Get JOB with our Free Placement Assistance Program
CTF Course in Bangalore
CTF Course in Bangalore by ICSS is the top-rated competitive course. The CTF competitors are highly demanded by organizations to penetrate networks and computer systems for finding and fixing security vulnerabilities. If you are considering working in the cybersecurity industry, then this training will benefit you greatly. CTF course in Bangalore is provided by cybersecurity professionals who are penetration testers at Indian Cyber Security Solutions. In the CTF course in Bangalore, you will master objectives including Intrusion Detection, Policy Creation, reconnaissance with Social Engineering and Google, DDoS Attacks, etc.
The categories of CTF include:
RE (reverse engineering):get a binary and reverse engineer it to search outa flag.
Pwn : get a binary and a link to a program running on a foreign server. Cause a buffer overflow, etc. to bypass normal functionality and acquire the program to read the flag to you.
Crypto :crypto means cryptography! Get an encrypted flag and work out a way to decrypt it (includes both classical and modern ciphers)
Web :web-based challenges where you’re redirected to an internet site, and you’ve got to search out and exploit a vulnerability (SQL injection, XSS, etc.)to urge a flag.
Forensics/ Stego :given a PCAP file, image, audio or other file, find a hidden message and find the flag. Other: this can be a small amount of a grab bag. Includes random puzzles, electronics-based things, OSINT, anything that doesn’t fit in to the opposite categories.
CTF 2.0 is the latest edition of our training. which provides the most advanced modules that connect to the real infrastructures in the organizations, and also assist students/professionals to prepare for global certification. This curriculum has been designed in such a manner. that it accommodates both freshers and specialists and provides them with the necessary training w.r.t their skills.
Need to Work on real-time projects and complete assignments to get Professional Certification from Indian Cyber Security Solutions
ICSS provides the course completion certificate once you successfully complete the CTF training program Professional Certificate Holders work at 1000s of companies like HP, TCS, Amazon, Accenture and many more.
REGISTRATION DESK
Current Job Openings
Check job profile, salary scale of current jobs available in market
Indian Cyber Security Solutions offers the best CTF training as they are the Best CTF Training Institute in Bangalore. We focus on the in-depth knowledge of the learners through our experts. Therefore, you will able to improve your knowledge of risks and vulnerabilities. At first, you have to think like a hacker to learn the skills. Indian Cyber Security Solutions delivers a 90% practical course by penetration testers who are themselves CEH certified and OSCP certified.
With this, Indian Cyber Security Solutions has made many students a professional in the field of Cyber Security. Achieving many important awards of the country. Indian Cyber Security Solutions have been acknowledged by Silicon India as one of the best Cyber Security Training Institute in the country. With this, we also provide Cyber Security services to corporate organisation as well. We have given the perfect security to organisation that has given them a negligible cyber security threats and hacks. With our services to organisations, Business Connect India has acknowledged us as the Top 10 Tech Brands of 2021
What does an organization expect from a Cyber Security Professional?
Our training module is delicately balanced between practical lab based training and theoretical content. Organizations expect real time practical based solutions to the real world threat of cyber attack. Focusing on practical training conducted by Bug Bounty hunters and exploit writers.
ICSS CTF training Course will surely give you the edge and help you to grab the job. Our ethical hacking training program also focuses on the most important aspect of “Documentation” / “VAPT Reporting”. Cyber security professionals will not only impart you with latest cyber security training but will also help you to prepare and report critical vulnerabilities to companies as a bug bounty hunter and also helps you in VAPT report writing.
For an organization a cyber security professional who has technical and as well as reporting / documentation skill will always be the first choice. This reduces the investment of organizations on the newly recruited cyber security professional.
CTF Training Institute in Bangalore
ICSS being the best CTF Training Institute in Bangalore will build your knowledge of the tools and techniques used by hackers. As a result, you will learn how malicious hackers use various tools. This certification is highly demanded by top companies as a prerequisite for information security-related job posts. So you should explore to advance your career to the top position in security. Get ahead on your career with in-depth and intensive training for CTF certification in Bangalore.
Types of challenges:
- Binary exploitation: comes all the way down to making an application act differently than how it had been intended to run. By making the application run differently, you're gaining valuable information that you're going to use to change or commandeer the target.
- Reverse Engineering: Reverse engineering challenges require an intimate knowledge debugger and disassembler software. The goal: Take a compiled binary, rip it apart, and learn how it works.
- Web Exploitation: These question types cover a good range of various methods to use web-based resources. While the methods are broad, there's are tools commonly related to web exploitation, including N-map, Wireshark, and Metasploit.
- Cryptography: Cryptography challenges are particularly fun. Even the definition for cryptography sounds fun. "Cryptography is that the practice and study of techniques for secure communication within the presence of third parties." In practice, however, they'll be difficult. Often enough, these questions are supported string conversions from one format to a different.
- Forensics: this kind of question in an exceedingly CTF environment can cover plenty of ground, but it's quite common that you will be asked to seek out files or information hidden within other file types. for example, an easy jpg or png file may well be manipulated to carry information like text, or maybe an executable.
Indian Cyber Security Solutions conducts campus placement drive for students within few months after completion of the cyber security course. ICSS conducts soft skills classes for students to enhance their soft skills which are highly required to crack interviews. Check out our placement records where we have displayed emails and letters which have come to us for conducting job interviews. MNC’s like PWC , ITC and CTS had recruited ICSS students since 2018. We sincerely believe that after the intense practical lab based training on cyber security conducted by ICSS you as an individual will definitely be self sufficient to crack any job which requires cyber security skills. CEHP course module is designed as per the industry demand which is evident from the job postings made by recruiting companies in different job portals.
CTF training Course in Bangalore and workshops conducted by ICSS Educational Division
CTF Training Course in Bangalore and workshops are conducted across all collages. ICSS had been fortunate enough to have been associated with some of the renounced educational institutions like IIT Kharagpur, NIT Durgapur, Jadavpur University, Lovely Professional University and JIS collage to name a few. Our campus representatives are highly active and conduct interactive sessions on cyber security. Campus representatives are student’s representatives from different collages those who are responsible for establishing a research lab on cyber security inside the campus of the respective collages. These research facilities & interactive sessions on ethical hacking helps the students to gain latest knowledge in cyber security. Indian Cyber Security Solutions offers CTF Training Course in Bangalore for corporate teams and individuals.
Do you want to be a Campus Representative?
If you want to be a CR there is a long list of benefits that you will be entitled too.