Web Security Company in Bangalore where Enterprises Trust ICSS Website Security Audit & Penetration Testing as a Service
Web Security Company in Bangalore is what all MNC’s and SME’s are looking for. As the risk of cyber threats and cyberattacks on web-based applications has considerably increased in the recent past. Staying protected is a challenging task in this Wild Wild Web (www) without undergoing an intense web security audit. A recent study done by Security Magazine states that there is an attack carried out by a malicious group of black hat hackers every 39 seconds on average on the web. The default username and passwords that are being used give hackers more chances of success.
Indian Cyber Security Solutions is proud to be rated among the best web penetration testing service providers in Bangalore providing manual based penetration testing and state of the art security solutions to your web-based applications. ICSS has secured 300+ website and web-based applications around the globe and had gained considerable experience backed by qualified professions having certifications on OSCP, CISSP, ISO-27001 Lead Auditor, and Certified Ethical Hacker.
Undergoing a penetration testing audit on a regular interval is highly required as threat actors are continuously looking for vulnerabilities to be exploited. In this cybersecurity industry, the largest gap among the managed service providers is a variable costing of penetration testing. ICSS aims to bridge the gap by having a quantified pricing structure for the web security audit & penetration testing.
PRICING PLANS FOR BLACK BOX TESTING
STANDARD PLAN
3,500 /-
(PER PAGE)
12 months
2 times VAPT
Cyber insurance 70%
Add minimum 5 extra Page for testing
PREMIUM PLAN
7,500/-
(PER PAGE)
24 months
4 times VAPT
Cyber insurance 75%
Add minimum 10 extra page for testing
Corporate training 1 times in a year (Duration: 1 week | 5 members)
SOC Support
PRICING PLANS FOR WHITE BOX TESTING
STANDARD PLAN
3,000 /-
(PER PAGE)
12 months
2 times VAPT
Cyber insurance 70%
Add minimum 5 extra Page for testing
PREMIUM PLAN
7,000/-
(PER PAGE)
24 months
4 times VAPT
Cyber insurance 75%
Add minimum 10 extra page for testing
Corporate training 1 times in a year (Duration: 1 week | 5 members)
SOC Support
Privacy Notice
Data shared by you will only be used to contact you with more details. Your personal data will not be shared with any third party at any circumstances.
Kolkata Office
Bangalore Office
Fill-up the Details
Bangalore has been known to be the Information Technology Capital of India and since the inception of the 21st Century, many more companies have been looking at this place as the most favourable place to invest. With the improvement in the city as well as nearby regions economic improvement, indicating a high number of literacy rate; the usage of IT devices and platform has been a lot. With this, MNCs like Dell, Accenture, Deloitte, HP, CISCO and various have established headquarters for India here. With this, the demand for Cyber Security Services are needed in both Multi National as well as Small and Medium Sector enterprises. ICSS, aims in providing network security services that is hack free. We have been expert in the field of Cyber Security since our inception, having worked for many reputed clients of Private organisation, Public Sector Organisation, Government Organisation as well as for E-Commerce Organisations.
Penetration testing can cost anywhere from $4,000-$100,000. On average, a high quality, professional pen test can cost from $10,000-$30,000. A lot of these costs are determined by factors such as: Size: A smaller, less complex organization is certainly going to cost less than that of a large company.
A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (WAF).
To Select a penetration testing company for web security audit, it is important to:
- Evaluate technology achievements of the vendor
- Focus on the vendor’s real knowledge and not just on certifications
- Evaluate the company’s trustworthiness and dependability
- Consider Cost vs. Frequency advantage
- Seek penetration testers (Specialists)
- Check the “Process” along with Pen Tester’s resume
- Flexibility and Turn Around time
- Can the vendor scale up to meet your peak demands?
A web application penetration test is a type of ethical hacking engagement designed to assess the architecture, design and configuration of web applications. Assessments are conducted to identify cyber security risks that could lead to unauthorised access and/or data exposure.
Penetration testing should be performed on a regular basis (at least once a year) to ensure more consistent IT and network security management by revealing how newly discovered threats (0-days, 1-days) or emerging vulnerabilities might be exploited by malicious hackers.
27001 is the best-known standard in the family providing requirements for an information security management system (ISMS). The ISO 27001 standard requires that security testing is conducted. As part of your ISO initial and annual compliance audit, your auditor will require evidence (such as a penetration test report) that you have conducted sufficient checks relating to security vulnerabilities. ICSS is a ISO 9001:2015 and 27001:2013 Certified Organisation.
Why Choose us ?
How Indian Cyber Security Solutions Team works?
Indian Cyber Security Solutions being one of the top-rated web security company in Bangalore follows certain steps which is highly important in the business of cybersecurity. Web Penetration testing VAPT service is an onsite service provided by ICSS where our teams of web applications penetration testers are invited by the enterprise at their testing site for the VAPT process. Indian Cyber Security Solutions aims at providing cyber security VAPT service to clients. Our team of technical experts assesses the critical infrastructure of the enterprise and provides valuable cyber security consultancy to the organizations.
ICSS helps the enterprise to implement cyber security measures as per the technical VAPT report provided by the penetration testers. Enterprises heavily rely on cyber security products for their critical infrastructure protection. Cyber Security Products like – anti viruses, IDS, IPS & Firewalls are highly capable to prevent intrusions only when they are implemented after manual security testing done by penetration testers. ICSS aims in helping out enterprises to allocate right budget for cyber security. VAPT services helps to find out the actual pain area of the organization and taking steps to patch vulnerabilities.
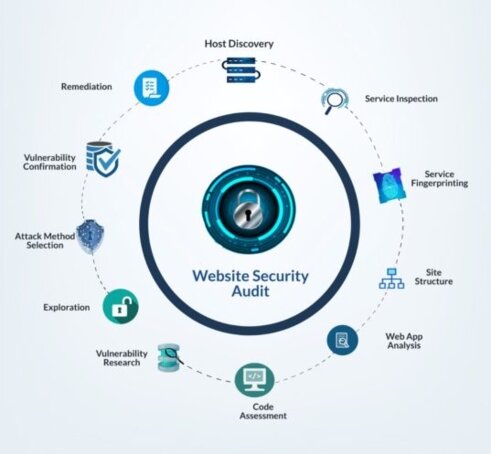
The security assessment is processed are as follows:
Note: After phase III if any additional vulnerabilities found during testing we will continue and move to phase II and follow the audit circle with no extra cost involved.
Indian Cyber Security Solutions your Trusted Partner for Web Application Testing
ICSS leads the industry in web application penetration testing, identifying vulnerabilities in a range of programming languages and environments. From web-based apps in highly scalable AWS environments to normal apps in traditional infrastructure, Our security experts have helped secure data across the world. Among the web security companies in Bangalore , ICSS has transformed the web application penetration testing market by focusing on reducing false-positive reporting through manual-based testing.
With dozens of zero-day vulnerabilities disclosed and our research circulating on national news outlets, we consistently prove our commitment to top-notch security testing.
Why should you undergo a Penetration Testing Audit for your Web-based Applications?
Indian Cyber Security Solutions offers web service testing, manipulating, and fuzzing parameters found in the WSDL. These configuration files provide a structure for SOAP (Simple Object Access Protocol) requests which the web service accepts – and to which it responds.
Strategic approach in web VA & PT makes Indian Cyber Security Solutions, as the favorite choice among the enterprises within all the web security company in Bangalore .

Security Testing following the OWASP Top 10 list and beyond
OWASP top 10 vulnerabilities are very critical level vulnerabilities in web-based applications and play a very vital role in website and web-based application security testing. Our testing team not only focuses on finding out critical level vulnerabilities as listed in the OWASP top 10 list but also finding out bugs that are critical in nature to the business.
We also follow SANS top 25 most vulnerability list for the web application penetration testing that we conduct for our clients.
Reporting the critical level vulnerabilities on a scale of 5 where five being the highest level of critical vulnerability and one being the low-level vulnerability. ICSS aims at providing a detailed analysis of the critical infrastructure through threat mapping and identifying the gaps in the infrastructure.
Understanding the security posture of the company is very important to determine the level of threat a threat actor can poses. In the entire process of vulnerability analysis and penetration testing our team aims at providing the best threat mitigation action to the enterprise.
ICSS has its own tool SAVE which is a Secured AI-based Vulnerability Assessment tool for Enterprise which is used to find our vulnerabilities in the company’s web-based applications. SAVE has made ICSS stand out from its competitors and had paved the way for becoming the leading web security company in Bangalore. While web services have many unique components and risks, they can also contain many of the same vulnerabilities as typical applications, such as SQL Injection. As a web penetration testing service providers in Bangalore ICSS had managed to gain considerable experience in securing more than 300+ Enterprises World Wide.
WEB APPLICATION PENETRATION TESTING Companies in Bangalore
Web application penetration testing companies in Bangalore that provide manual based application testing are very less. Indian cybersecurity solution is fortunate enough to have a team that is equally talented and hard-working. With team members names enlisted as exploit writers in Exploit DB and having them in the list of Hall of Fames of different MNC’s like CISCO, Microsoft, Amazon, and Facebook to name a few makes the technical team of Indian Cyber Security Solutions more robust and equally experienced where you can trust Strategic approach in web Vulnerability Assessment and Penetration Testing makes Indian Cyber Security Solutions as the favorite choice among the enterprises among all the web security company in Bangalore .
ICSS Web Pen-Testing Methodology
ICSS is proud to have served clients from varied domains like the hospital industry, government agencies, financial institutions to large e-commerce portals. Experienced penetration testers carry out the VAPT process with all the modern technologies which are used in the penetration testing industry.
Web Application penetration testing is carried out with prerecession by the team of ethical hackers and penetration testers where we follow the OWASP top 10 vulnerabilities and also covering critical vulnerabilities that are vital to the business.
Among the best Web application penetration testing companies in Bangalore , ICSS operates under a structured, repeatable methodology. We prioritize this concept in each engagement to make certain that our assessment is reliable, reproducible, and top-notch in quality. As such, our findings can always be verified by your team, before and after the remediation.
STEPS & STAGES OF WEB APPLICATION SECURITY TESTING
Steps that make INDIAN CYBER SECURITY SOLUTIONS the leading web security company in Bangalore
WHAT IS THE ACTUAL WEBSITE SECURITY AUDIT COST IN Bangalore ?
Website Security Audit Cost in Bangalore depends on testing methods - Manual, Automated, or Both.
Website security audit cost in Bangalore is a bit confusing as companies demand as per their wish with very little clarity on the deliverables. Understanding the difference between what promised and priced according to the deliverables is highly critical for clients.
The testing approach does play a very vital role in actually evaluating the pricing set by the web security company in Bangalore . Both manual and automated approaches to penetration testing have value, and we use both.
Automation is necessary for full testing coverage, and in some cases is actually better than manual testing. Automation by itself, however, is entirely incapable of identifying, let alone validating, some of the most important security flaws found in web applications.

ENSURING CUSTOMER TRUST BY FOLLOWING CERTAIN STEPS
As the requirement and search for the best web application penetration testing companies in Bangalore increases. ICSS focuses on providing what the enterprise needs in the most professional manner. Conducting VAPT on web-based applications in a phased manner. Indian Cyber Security Solutions takes clients' data privacy very seriously. Once the scope of the work is finalized between ICSS and the client, they are requested to sign up for an NDA agreement.
Is your Web Application Firewall strong enough to protect your data?
CHECK YOUR BUSINESS WEBSITE AND GET A SCAN REPORT
Check out the Demo Web Application Penetration Testing Report:
Website Security Audit Company in Bangalore - How ICSS Team Works?

Website security Audit Company in Bangalore providing in-depth manual based security testing on web based applications. Indian Cyber Security Solutions being one of the top-rated web security company in Bangalore follows certain steps which are highly important in the business of cyber security.
Web Penetration testing VAPT service is a remote service provided by ICSS where our teams of web application penetration testers take the full access of the web based application from our research and development center located in Bangalore and in Kolkata or can be invited by the enterprise at their testing site for the VAPT process.
Indian Cyber Security Solutions aims at providing cyber security VAPT service to clients. Our team of technical experts assesses the critical infrastructure of the enterprise and provides valuable cyber security consultancy to the organizations. ICSS helps the enterprise to implement cyber security measures as per the technical VAPT report provided by the penetration testers.
Enterprises heavily rely on cyber security products for their critical infrastructure protection. Cyber Security Products like anti-viruses, IDS, IPS & Firewalls are highly capable to prevent intrusions only when they are implemented after manual security testing done by penetration testers. ICSS aims in helping out enterprises to allocate the right budget for cyber security. VAPT services help to find out the actual pain area of the organization and taking steps to patch vulnerabilities.
Web Security Application Pen Test Tools used by Indian Cyber Security Solutions while conducting a web security audit
The primary tools we use for Web Application Penetration Testing are:
- Web Browsers
- Burp Suite Professional
- SoapUI
- Custom Perl Scripts
- Custom Python Script
- Python GO script
This is not a complete list, but these are the major tools. We look for simple, powerful, flexible and proven tools. As the leading website security audit company in Bangalore , ICSS explains in details about the tools used in conducting the audit.