Social Engineering - ICSS
The term "Social Engineering" refers to a wide range of malevolent behaviours carried out through human relationships. It employs psychological manipulation to dupe users into committing security errors or disclosing sensitive information.
Social engineering assaults can be carried out in one or more steps. A perpetrator first analyses the target victim to obtain background information, such as potential points of entry and lax security standards, that will be required to carry out the attack. The attacker then proceeds to acquire the victim's trust and give stimuli for further acts that violate security norms, such as disclosing sensitive information or granting access to key resources.
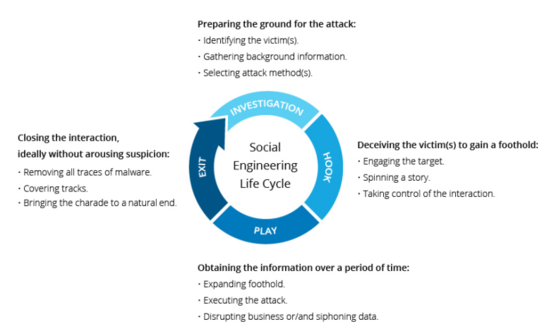
What makes social engineering so hazardous is because it relies on human error rather than software and operating system flaws. Legitimate user errors are far less predictable, making them more difficult to detect and prevent than malware-based intrusions.
Social Engineering Attack Techniques
Social engineering assaults can take many different forms and can be carried out everywhere there is human interaction. The five most prevalent types of digital social engineering attacks are as follows.
Baiting
Baiting attacks, as the name implies, use a false promise to spark a victim's avarice or curiosity. They trick people into falling into a trap that takes their personal information or infects their computers with malware.
The most despised kind of baiting involves the use of tangible media to disseminate malware. For example, attackers may place the bait (usually malware-infected flash drives) in high-traffic areas where potential victims are bound to see them (e.g., bathrooms, elevators, the parking lot of a targeted company). The bait has a genuine appearance, such as a label that presents it as the company's payroll list.
Out of curiosity, victims pick up the bait and insert it into a work or home computer, resulting in the automated installation of malware on the machine.Baiting schemes may not always have to take place in the actual world. Baiting online takes the form of appealing adverts that direct viewers to harmful websites or entice them to download a malware-infected application.
Scareware
Scareware bombards victims with false alerts and phoney threats. Users are duped into believing their system is infected with malware, prompting them to install software that provides no real value (except to the perpetrator) or is malware itself. Scareware is also known as ruse software, rogue scanner software, and fraudware.
A frequent example of scareware is the appearance of legitimate-looking popup advertisements in your browser while surfing the web, with language such as, "Your machine may be infected with nasty spyware applications." It either offers to install the utility (frequently tainted with malware) for you or directs you to a malicious site where your machine becomes infected.
Scareware is also disseminated through spam email, which sends out fake warnings or offers consumers worthless/harmful services.
Pretexting
In this case, an attacker collects information by telling a succession of carefully designed lies. A perpetrator would frequently commence the scam by professing to require sensitive information from a victim in order to complete a key assignment.
The attacker usually begins by gaining trust with their target by impersonating coworkers, police officers, bank and tax authorities, or other individuals with right-to-know authority. The pretexter asks inquiries that are apparently required to validate the victim's identity, allowing them to obtain sensitive personal information.
This fraud collects all kinds of relevant information and records, including social security numbers, personal addresses and phone numbers, phone records, employee vacation dates, bank records, and even security information relating to a physical plant.
Phishing
Phishing scams are email and text message campaigns that try to create a sense of urgency, curiosity, or terror in victims. They are one of the most common types of social engineering attacks. It then manipulates individuals into disclosing personal information, clicking on links to fraudulent websites, or opening attachments containing malware.
An example is an email sent to subscribers of an online service informing them of a policy violation that necessitates prompt action on their side, such as a password change. It contains a link to an illicit website that looks virtually identical to the official version, inviting the unsuspecting user to input their current credentials and a new password. When you submit a form, the information is delivered to the attacker.
Given that phishing campaigns send similar or nearly identical messages to all users, detecting and blocking them is significantly easier for mail servers with access to threat sharing services.
Spear phishing
This is a more targeted variation of the phishing scam in which an attacker selects certain persons or businesses to target. They then customise their communications to their victims' features, employment positions, and contacts in order to make their attack less visible. Spear phishing necessitates far more work on the part of the perpetrator and can take weeks or months to complete.
They are far more difficult to detect and have a higher success rate if done correctly.In a spear phishing scenario, an attacker sends an email to one or more employees while impersonating an organization's IT consultant. It's worded and signed exactly like the consultant usually does, leading recipients to believe it's a legitimate message. The letter instructs recipients to update their passwords and includes a link that takes them to a fraudulent page where the attacker steals their credentials.
Social Engineering Prevention
Social engineers use human emotions like curiosity or terror to carry out schemes and lure victims into their traps. As a result, be cautious if you receive an alarming email, are drawn to an offer shown on a website, or come across loose digital media laying around. Being vigilant can help you protect yourself from the majority of social engineering attempts that occur in the digital arena.
Furthermore, the following pointers can assist you increase your alertness in connection to social engineering hacks.
- Don’t open emails and attachments from suspicious sources – You are not required to respond to an email if you do not know the sender. Even if you know them and are sceptical of their message, cross-check and corroborate the information from other sources, such as the telephone or the website of a service provider. Remember that email addresses are constantly spoofing; even an email allegedly from a trusted source could have been launched by an attacker.
- Use multifactor authentication– User credentials are one of the most valuable pieces of information that attackers want. Using multifactor authentication helps to protect your account in the case of a system intrusion. Imperva Login Protect is a simple 2-factor authentication solution that helps improve account security for your applications.
- Be wary of tempting offers– If an offer sounds too good to be true, think twice before accepting it. You can rapidly evaluate whether you're dealing with a legitimate offer or a trap by Googling the topic.
- Keep your antivirus/antimalware software updated – Make sure that automatic updates are turned on, or make it a practise to download the most recent signatures first thing each day. Check to ensure that the updates have been deployed on a regular basis, and scan your system for any infections.
Why Choose Indian Cyber Security Solutions (ICSS) ?
Indian Cyber Security Solutions is one of best institute of India among other institute in India. ICSS offer as CEHv11 Courses in India as well as kali Linux. ICSS has won as many award for giving the online training as well as offline training. Its way of giving the training is unique which is easily adapted by the student as well as the professional. Due to way how ICSS trained the student it has got as many award some of award are Tech Brand of 2020, Ten most trusting cyber security certification provider 2021 and many more.
Among the many Ethical Hacking course in India, Indian Cyber Security Solutions would be the right for you to join. We have the right set of practical lab classes set up for students to learn as well as industry grade trainers who would conduct the classes and impart the right set of Cyber Security Knowledge to students. Our efforts have been acknowledged by various reputed administrative institutes, such as "Top Ten Training Institutes in India in 2020” by Silicon India; as well as Ten Most Trusted Training & Cyber Security Certifications Provider, 2021 by The Knowledge Review.
We not only provide ethical hacking course, but also Machine learning, Java Programming, AWS Cloud Computing, Microsoft Azure, OSCP, CISSP, Networking and more. As these encompasses Cyber Security, we make sure that we provide a 360 view of Cyber Security courses.
As an Education Institute, we are also cyber security service provider to corporate organization. Services like VAPT, Web Penetration Testing, Network Penetration Testing, Mobile Application Penetration Testing to corporate organization like IRCTC, HDFC, Cambridge Technologies, and many more. With this, Indian Cyber Security Solutions have been acknowledged as the 20 Tech Brands of 2021. by Business Connect India.
Our Cyber Security Services
Cyber Security is extremely important for every organisation and that we understand that data theft avoided is better than data theft done. Thus we also provide cyber security services to various MNCs across India. Our team is professional in providing Web Application Penetration Testing, Network Penetration Testing, Mobile Application Penetration Testing to clients.
We this, we have been acknowledged as the top 20 most Cyber Security Trusted Brands for 2021 by The Global Hues. We stand by to our commitment in providing the right cyber security training to students. We have provided services to clients like Madhya Pradesh Gramin Bank, Odisha State Pollution Control Board, HDFC Life Insurance Corporation, Qatar Development Bank and many more.
Why not Enquire more about our Education Training and Corporate Services?
CERTIFIED COMPANY


MEMBER OF



OUR ADDRESS
KOLKATA
Globsyn Crystals Building,5th Floor, Unit-4, Webel MoreKolkata – 700091
BANGALORE
Chirush Mansion, 3478J HAL 2nd Stage,13th A Main Road Indiranagar Bangalore – 560008 Land Mark: Behind New Horizon School
CANADA141E34
Indian Cyber Security Solutions Cyber Security Research & Analytics Center Vine Avenue Moncton NB,Canada, PO E1E 1J9
AUSTRALIA
Indian Cyber Security Solutions Australia (Research and Development Center)11 Darling Street, Hughesdale Melbourne VIC. 3166
© 2021 Indian Cyber Security Solutions | Green Fellow IT Security Pvt. Ltd.