Red team assessment service provider in India – Red Teaming Service for Enterprise
Red team assessment service provider in India aims to compromise critical assets in company’s network, multiplying the vast scope of an external attacker would have. As a leading red teaming cyber security engagement service provider in India, ICSS has developed a world-class team of offensive security engineers and researchers. Red Team Assessment Services are highly critical for enterprises who want to test the security posture of the organization.In recent years the cyber attacks on the enterprise-critical assets have seen a huge rise. Critical data have been leaked even though the organizations have invested millions of dollars in a wide range of security & monitoring solutions.

How red teaming different from penetration testing?

Indian Cyber Security Solutions has been acknowledged as one of the leading Top 20 Tech brands in India for 2021 by Business Connect India
ICSS Red Teaming Service for Enterprise Security
ICSS-Red Team provides a comprehensive threat and vulnerability/penetration assessments. Red teaming is essential in securing organizations critical assets. Our Red Team Penetration testing starts with a clear understanding of organizations vulnerabilities where vulnerability Assessment & Penetration Testing plays a very essential role.
Indian Cyber Security Solutions is fortunate enough to have been associated with top brands in providing red team exercises on both corporate office and industrial plant locations. ICSS have the resources, methodology, and experience to perform these tests in a safe manner that does not impose any operational risk to our clients.With our red team we will perform Application Penetration Testing, Network Penetration Testing, Vulnerability Testing, Phishing Testing, and Social Engineering to find the weak spots in your critical assets/employees and recommend corrective action before attackers can exploit them to sabotage your business or steal your confidential data.

* We don’t share your personal info with anyone. Check out our Privacy Policy for more info.
Red Team Cyber Security Assessments at a Glance:
We help you:
What you get:
Red Team Penetration Testing is the need of the hour to ensure organizations data security
Red team penetration testing is highly critical in nature as constant application updates and changes to application and system configurations can introduce vulnerabilities and leave you susceptible to an attack, even if you are keeping your security controls up to date. ICSS being the leading red team assessment service provider in India focuses on key factors where attack simulations go beyond testing an organization’s IT controls involving its people, processes and technologies.But a red team assessment is not for everyone and is usually performed by organizations with mature security programs (i.e. positive penetration test results, controls to detect security events, a security-aware culture). A penetration test is more suited for organizations that are still in the early stages of their security program and are looking to identify insecure business processes, poor security settings, or other weaknesses that a hacker could easily exploit.To keep your data secure, you must include continuously red teaming exercises to scan and test your systems and devices to detect vulnerabilities as they arise.
Benefits of Red Team Penetration Testing
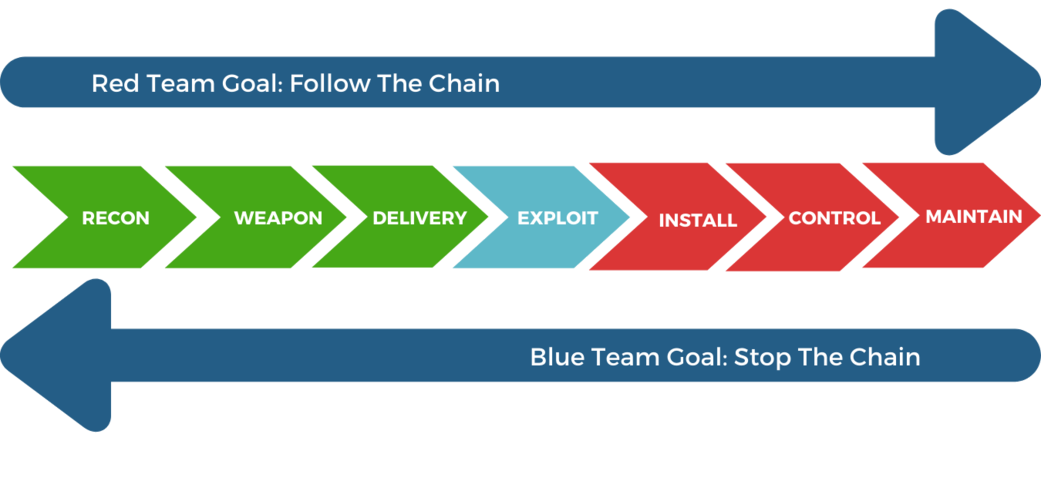
Methodology for the Red Team Penetration Testing
A red teaming operation can be difficult to structure due to the number of variables, hence we follow a set framework so you always know what to expect at the end.
Red Team Assessment Services to assess the security posture of the organization
Red Team Assessment Services follow the process of testing policies, plans, assumptions, and systems. Red Teaming is Ethical Hacking, performed without already informing the employees or preparing the existing systems in any way. This simulates a very real situation of how the company would panic in case of an attack, at this very moment.A red team exercise can be thought of as a compilation of our core services into one formidable package. ICSS expert consultants follow vulnerability from discovery and exploitation, to the detection and mitigation capabilities of the enterprise security architecture. We follow a comprehensive risk-based approach to manually identify threats and vulnerabilities in your networks, hosts, systems, applications and physical assets.
Red team assessment services are the most advanced security test your company can undertake and simulates a full scale, tailored attack on your organization. ICSS being the red team assessment service provider in India aims at testing your security against real-world attacks without the risks of negative headlines.
Why Organizations need Red Team Assessment Services?
Advanced Persistent Threats [APTs] can’t be relieved by standard security programming’s like firewalls and antivirus, and they are intended to highly affect associations, which consolidate to speak to high hazard to any association that is profoundly dependent on ICT, has huge data resources and basic IP, or are dependent upon web platforms for client interface and transactions.Associations must acknowledge that APTs are probably going to be fruitful and in this way think about the suggestions and likely attack situations.
A few firms will guarantee mindfulness however their full thought is deficient. Red Team Assessment Services is the necessity of organizations to get insured from the real-world attack.Hiring an external agency of “hackers” to break into your computer systems, on which you have spent millions of dollars to secure, seems like a really absurd plan. But sometimes, the best way to know if your system is secure is to find someone capable enough to try and break-in.