Broken Authentication OWASP Top 10 - A2 - ICSS
What is Broken Authentication?
This is about the Broken Authentication OWASP Top 10 - A2. These flaws can allow an attacker to capture or circumvent the authentication procedures employed by a web application:-
- Allows automated attacks like credential stuffing, in which the attacker has a list of legitimate users and passwords.
- Allows for brute force and other automated attacks.
- Allows for default, weak, or well-known passwords like "Password1" or "admin/admin".
- Uses insecure or poor credential recovery and forgot-password procedures, such as "knowledge-based answers," which cannot be secured.
- Passwords are used in plain text, encrypted, or weakly hashed form (see A3:2017-Sensitive Data Exposure).
- Multi-factor authentication is either absent or ineffective.
- Session IDs are exposed in the URL (e.g., URL rewriting).
- After a successful login, Session IDs are not rotated.
- Session IDs are not correctly invalidated. During logout or a period of inactivity, user sessions or authentication tokens (especially single sign-on (SSO) tokens) are not correctly expired.

An attack's purpose is to take over one or more accounts and gain the same rights as the attacked user.
BROKEN AUTHENTICATION EXAMPLES
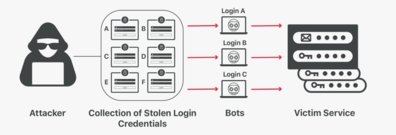
Example #1: Credential stuffing
A frequent attack is the use of lists of known passwords. If an application lacks automatic threat or credential stuffing measures, it can be exploited as a password oracle to assess whether the credentials are valid.
Example #2: Application session timeouts are not appropriately configured.
A user accesses an application from a public computer. Instead of clicking "logout," the user closes the browser tab and walks away. An hour later, an attacker uses the identical browser, and the user is still authenticated.
Example #3: Passwords are not hashed or salted properly.
An insider or an external attacker gains access to the password database of the system. User passwords are not hashed or salted properly, exposing each user's password.

Risk
In addition to being encrypted, stored username and password values should be salted and hashed.
How to prevent Broken Authentication
Broken Authentication
- Implement multi-factor authentication whenever possible to prevent automated, credential stuffing, brute force, and stolen credential re-use attacks.
- Do not ship or install any default credentials, especially for administrative users.
- Implement weak password tests, such as comparing new or updated passwords against a list of the top 10,000 worst passwords.
- Align password length, complexity, and rotation rules with NIST 800-63 B's Memorized Secrets standards in section 5.1.1 or other modern, evidence-based password policies.
- Use the same messages for all outcomes to protect the registration, credential recovery, and API pathways against account enumeration attacks.
- Limit or gradually postpone failed login attempts. All failures are logged, and administrators are notified when credential stuffing, brute force, or other assaults are detected.
Why Choose Indian Cyber Security Solutions (ICSS) ?
Indian Cyber Security Solutions is one of best institute of India among other institute in India. ICSS offer as CEHv11 Courses in India as well as kali Linux. ICSS has won as many award for giving the online training as well as offline training. Its way of giving the training is unique which is easily adapted by the student as well as the professional. Due to way how ICSS trained the student it has got as many award some of award are Tech Brand of 2020, Ten most trusting cyber security certification provider 2021 and many more.
Among the many Ethical Hacking course in India, Indian Cyber Security Solutions would be the right for you to join. We have the right set of practical lab classes set up for students to learn as well as industry grade trainers who would conduct the classes and impart the right set of Cyber Security Knowledge to students. Our efforts have been acknowledged by various reputed administrative institutes, such as "Top Ten Training Institutes in India in 2020” by Silicon India; as well as Ten Most Trusted Training & Cyber Security Certifications Provider, 2021 by The Knowledge Review.
We not only provide ethical hacking course, but also Machine learning, Java Programming, AWS Cloud Computing, Microsoft Azure, OSCP, CISSP, Networking and more. As these encompasses Cyber Security, we make sure that we provide a 360 view of Cyber Security courses.
As an Education Institute, we are also cyber security service provider to corporate organization. Services like VAPT, Web Penetration Testing, Network Penetration Testing, Mobile Application Penetration Testing to corporate organization like IRCTC, HDFC, Cambridge Technologies, and many more. With this, Indian Cyber Security Solutions have been acknowledged as the 20 Tech Brands of 2021. by Business Connect India.
Our Cyber Security Services
Cyber Security is extremely important for every organisation and that we understand that data theft avoided is better than data theft done. Thus we also provide cyber security services to various MNCs across India. Our team is professional in providing Web Application Penetration Testing, Network Penetration Testing, Mobile Application Penetration Testing to clients.
We this, we have been acknowledged as the top 20 most Cyber Security Trusted Brands for 2021 by The Global Hues. We stand by to our commitment in providing the right cyber security training to students. We have provided services to clients like Madhya Pradesh Gramin Bank, Odisha State Pollution Control Board, HDFC Life Insurance Corporation, Qatar Development Bank and many more.
Why not Enquire more about our Education Training and Corporate Services?
CERTIFIED COMPANY


MEMBER OF



OUR ADDRESS
KOLKATA
Globsyn Crystals Building,5th Floor, Unit-4, Webel MoreKolkata – 700091
BANGALORE
Chirush Mansion, 3478J HAL 2nd Stage,13th A Main Road Indiranagar Bangalore – 560008 Land Mark: Behind New Horizon School
CANADA141E34
Indian Cyber Security Solutions Cyber Security Research & Analytics Center Vine Avenue Moncton NB,Canada, PO E1E 1J9
AUSTRALIA
Indian Cyber Security Solutions Australia (Research and Development Center)11 Darling Street, Hughesdale Melbourne VIC. 3166
© 2021 Indian Cyber Security Solutions | Green Fellow IT Security Pvt. Ltd.